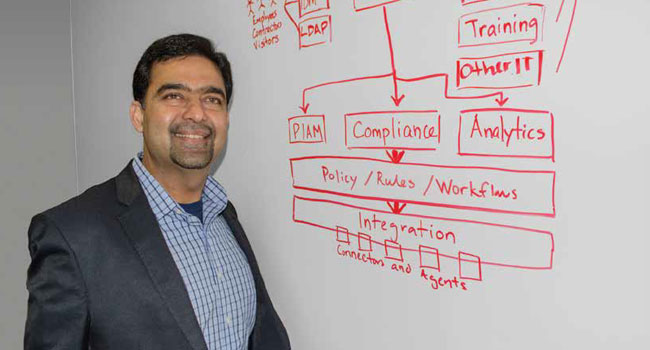
Safe and Secure
- By Ralph C. Jensen
- Mar 01, 2015
Jumping into the security industry was a calculated
and well-planned venture for Quantum
Secure. In fact, company president and
CEO, Ajay Jain, walked a few tradeshows
and talked to potential customers before making
the leap.
Taking the plunge in 2005, Quantum Secure’s
truly disruptive and innovative thinking led them
to introduce the industry’s first physical identity
and access management (PIAM) platform, along
with its SAFE software suite. Symantec Corporation
became their first customer in 2007, and the
rest is history. Quantum Secure is now known as a
leader for managing the physical security identity
lifecycle and automating the associated access privileges
and processes such as compliance to regulations,
on/off-boarding and identity analytics.
“As part of the SAFE software suite, we have
created a host of enterprise applications that help
automate physical security functions such as physical
identity management, role-based access, selfservice
access administration, audit and compliance
management into a single, web-based interface that
is easy to manage and use,” Jain said. “Customers
walk away with automated processes from HR to
the doors, thereby decreasing the risk posture of the
organization and related operational cost.”
To Market with Partnerships
By getting SAFE to the market, Quantum Secure has
partnered with many industry leaders in both the
physical and logical security space including Tyco,
Siemens, Johnson Controls, United Technologies/
Lenel, HID, Oracle, Microsoft, SAP, etc. to provide
a best-in-class experience in solution deployment
and consulting to organizations worldwide.
“Physical security departments are now
plugged into the corporate backbone along with
their IT counterpart to manage overall risks and
compliance disciplines,” Jain said. “They no longer
operate in silos, and PIAM is that glue.”
The adoption of the PIAM “glue” is increasing
dramatically in the corporate, government and semigovernment
world; however, not all dealers, integrators
or consultants are plugged in yet. Additionally,
the level of SAFE deployment requires hands-on
training by professionals who are IT-security savvy
with business process re-engineering skills.
Customers that show a need to manage compliance
with industry or internal standards have
shown a preference to include SAFE. Several large
international airports including San Francisco International,
Phoenix, Seattle and Toronto’s Pearson
International Airport have adopted SAFE to
automate their badging process and manage the
complexities of complying with TSA and related
regulations. With thousands of credentials issued
and managed monthly, San Francisco Airport, for
example, reported that they reduced processing
time by 35 percent in just the first year using the
solution, translating to $14 per credential. Many
large corporate customers like Oracle, AT&T,
Adobe, Symantec, United Health, General Motors
and Visa are also reaping benefits from the SAFE
software suite. In addition, federal government
agencies using SAFE software suite include the
Departments of Energy, Health and Human Services,
and the Food & Drug Administration. And,
because of its unique recommendations and mandates,
the PIAM/SAFE Software value proposition
applies to many other vertical markets like financial
institutions, health care and oil & gas.
Dealers and integrators have seen this product
from the outside looking in but are encouraged to
learn more about Quantum Secure and the SAFE
software suite. In fact, Quantum Secure reaches
out to integrators and dealers at tradeshows, offering
webinars and training for interested integrators.
They also provide training for sales teams of
any interested integrator.
“Early partners were mostly project driven,
but now several of those partners are creating
new high margin offerings with PIAM,” said Don
Campbell, director of product Management at
Quantum Secure. “These partners are proactively
bringing PIAM’s disruptive innovation to their
customer base by examining their long standing
security processes and using SAFE to reduce risk
and improve efficiencies.”
A Secure Environment
for Financial Services
Banks and other financial institutions must maintain
a secure environment. In order to do so, regulations,
such as Sarbanes Oxley and GLBA, must
be met across their physical and IT systems infrastructure.
Identities and related-area access has to
be managed within the physical and logical security
pyramid.
“Physical identity and access management is a
cornerstone of any financial institution’s security
plan,” Jain said.
The financial institution’s security managers
rely on their IT department to custom build pieces
of PIAM solution - as a Band-Aid fix. This is an
opportunity for dealers and integrators. For an
integrator, introducing the SAFE software suite to
their customer means introducing automatic processes
of managing internal controls and reducing
corporate risks.
The software helps reduce time, effort and operating
costs relating to the management of identities
by automating key functions. For a bank or financial
institution, SAFE provides a robust approach in
identity life-cycle automation, more transparency
in compliance and better understanding of security
operations via enhanced reporting.
“SAFE for finance addresses the highly stringent
compliance and security needs of the financial
market while allowing integration of disparate
systems for end-to-end identity management,
including advanced visitor identity management
functionality and executive-level reporting and
analytics,” Jain said.
Exceptional ROI for Sm all to
Medium-sized Business (SMB)
Literally, everything technology in the security industry
evolves. Software and hardware manufacturers
seek to add greater value to their solutions.
Customers push to cut costs while striving to reduce
risks and SAFE for Secure Cloud PIAM solutions
are geared to do exactly that: providing SAFE
capabilities and hosted IT infrastructure with
partners like Amazon AWS to drive costs down
and efficiencies up. Users can be up and running
quickly without dedicated software and servers.
SMBs also are able to easily integrate their cloud
PIAM solution with human resources, contractor
management, training, physical access control and
numerous other security systems already in place.
“This is an extremely powerful solution for
SMBs,” Jain said. “Cloud-based PIAM solutions
deliver exceptional return on investment, further
increasing their value by reducing total cost of
ownership, over time.”
Managing Growth in Large
Enterprise Businesses
Some large businesses have inherent problems of
managing growth along with diverse IT and physical
security infrastructure. They have typically
grown organically and through acquisitions over
time, assimilating a variety of identity types and
heterogeneous systems infrastructure, business
processes and view of corporate risks. They need
PIAM glue to bring all processes, systems and
regulatory requirements into a common platform.
There also is something else large businesses
can take advantage of: predictable insights. Advanced
PIAM solutions are geared to provide intelligence
about our security processes specifically to
better understand risk, early indicators of security
compromise and find process inefficiencies where
we can cut costs. Predictive intelligence will detect
and identify irregular behavior based on set policies
and parameters. Once anomalies are detected,
security management is able to investigate perceived
threats and control outcomes proactively.
Managing Access Privileges
in Healthcare
There are numerous reasons that managing access
privileges for visitors, contractors and vendors in
a hospital setting is challenging. Typically, visitor
management is complicated because of facility layout
but also because of the population of people in
the complex. Hospitals usually consist of numerous
buildings on a sprawling campus, and identity
management must comply with growing requirements
of compliance.
“Fortunately, the growth of intelligent and
purpose-built, automated visitor identity management
(VIM) software provides a solution to
address these challenges,” Jain said. “Integrators
should know this is a ready-made solution for
healthcare. Centralized VIM solutions can add
depth to the hospital’s overall administrative safety
and security operations, offering the right access to
the right areas for the right length of time.”
Few other industries must meet the regulations
that healthcare does. Centralized VIM can help
ease the pain by automating compliance initiatives
to specific standards.
The use of PIAM also is on the rise in the healthcare
setting. Integration of PIAM will keep an eye
on several driving concerns: controlling access to
restricted areas; limiting risks, especially abductions
and elopements; and maintaining compliance
with HIPAA standards. No one wants to see
or hear about abductions from a hospital; however,
on average, five infants per year are abducted from
U.S. hospitals, and in some cases, despite the use
of high-tech security bracelets. More mobile patients
determined to be mentally, developmentally
or emotionally impaired, or who are addicted to
drugs are the types of people who may attempt to
elope from a facility.
Incorporating an intelligent, identity-based
management solution provides enhanced security
by automating verification in addition to screening
and badging identities throughout healthcare facilities. Credentials can be incorporated into ID
bracelets or other wearable badges,
and PIAM provides a reliable platform
to manage these policies. Additionally,
PIAM will ensure that
HIPAA requirements, regarding
physical access to sensitive data, will
be met to maintain privacy and security
of an individuals’ identifiable
health information.
Education - A Couple
of Mini Case Studies
Johnson Controls, an integrator,
installed Quantum Secure’s SAFE
identity management system at Roger
Williams University. The solution
serves as an interface between the
P2000 security management systems
and the university’s enterprise resource
planning system that houses
all the information about where students
need to be and when.
With SAFE in place, the university
saves many man-hours, and now
uses that time for other ongoing tasks
such as setting up alarm upgrades,
securing additional entrances and
replacing or re-keying necessary
physical lock hardware.
SAFE automates nearly 40 percent
of the security operations at Roger
Williams University, potentially
eliminating as much as 95 percent
of the errors associated with manual
processing. Cycle time and change
requests have also improved.
Similarly, Siemens brought the
SAFE solution to Southern Methodist
University (SMU) to automate their
complex internal identity- and access
management-related processes.
The identity management solution
also helps SMU maintain and
improve internal policies and procedures
related to the physical security
of all staff, property and assets.
Accuracy of access assignments has
improved and means that the right
people are in certain places at certain
times, which improves not only security,
but also accountability.
While Quantum Secure started
operations working with much larger
companies and international airports,
the brand is rapidly gaining
traction in smaller markets equally.
For instance, a smaller airport must
meet the same TSA criteria as a much
larger international airport. The same
policies must be in place. Similarly
in the SMB market, the challenges
are exactly the same as for the larger
businesses. Just the scale is less.
Quantum Secure is a well-known
solution in the security industry. Company
officials are able to work with a
wide spectrum of key players. They are
able to communicate with IT security
staff and assist in business process reengineering
wherever required, and
have a desire to help integrators better
understand how to be SAFE.
“Today SAFE is managing very
large, complex customers where
the volume on a daily basis could
be over one million identity-related
transactions as well as smaller businesses
where the volume is under
500 transactions,” Jain said. “It’s the
same SAFE software managing both
environments; the scale is different
but the benefits are the same. SAFE
is reducing risks and lowering operating
costs.”
This article originally appeared in the March 2015 issue of Security Today.