New Ransomware Attack Infects Airlines, Banks and Utilities across the World
Yesterday, PC users across the world were asking for help as ransomware took data hostage and locked users out of their computers.
A major ransomware attach brought business to a close throughout Europe just weeks after the major WannaCry Attack. The most severe damage is being reported by Ukraine, with compromised systems at the central bank, state telecom, municipal metro and airport. Systems were also reported infected at the country’s electricity supplier, although a spokesperson for the power supply company said they remained unaffected during the attack.
The virus spread internationally in a matter of hours. Danish shipping company Maersk reported systems down across multiple sites, including the company’s Russian logistics arm Damco. Also in Russia, the virus reached severs for oil company Rosneft, although it is unclear how much was damaged.
In addition to the infected computer systems overseas, several U.S. companies were affected by the ransomware, namely pharmaceutical company Merck, a Pittsburgh-area hospital and the U.S. officers of law firm DLA Piper.
Reports from a Kaspersky researcher identified the virus as a variant of the Petya ransomware, although later remarked that the strain was completely new. After that, the ransomware became dubbed as “NotPetya.”
NotPetya works similarly to WannaCry, as it spreads quickly through Window’s SMB file-sharing system, taking the data hostage and asking users to pay a ransom to get it back.
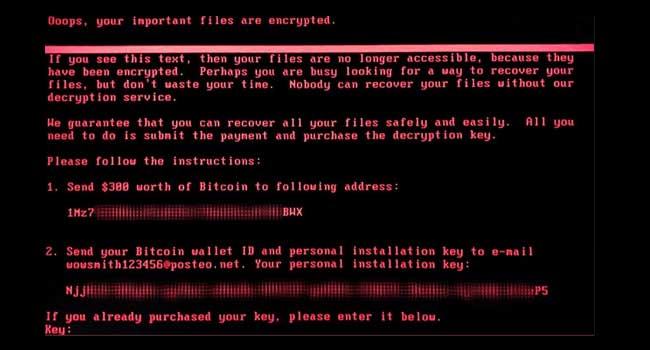
Once infected, the virus encrypts each computer to a private key, rendering it unusable until the system is decrypted. The program then instructs the user to pay $300 to a static Bitcoin address, then email the bitcoin wallet and installation key to a Posteo email address. As of yesterday afternoon, blockchain records showed 20 transactions to the target wallet, totaling roughly $4,900. It’s unclear whether any systems have been successfully decrypted after payment.
Windows sent out a security patch following the WannaCry Attack, but many users remain vulnerable. It seems a string of malware variants have employed the exploit to deliver ransomware or mine cryptocurrency.