i-PRO Shares IoT Pillars of Cybersecurity for Cybersecurity Awareness Month
Featuring four pillars that should be the foundation of any IoT security program
i-PRO Co., Ltd is proud to join with the Department of Homeland Security Cyber and Infrastructure Security Agency (DHS CISA) to raise awareness around cybersecurity for NCSAM (National Cyber Security Awareness Month). The world has seen significant increases in cyber-attacks aimed at critical infrastructure and security products in the last few years, with IIoT (Industrial Internet of Things) devices such as security cameras, becoming prime targets for hackers.
According to a Kaspersky analysis of its telemetry from honeypots shared with Threatpost, in first half of 2021 alone, there were over 1.5 billion IoT breaches. This statistic is just the recorded number, meaning the actual number is probably much higher. It is clear that IoT and IIoT manufacturers must do more to help secure these devices and educate the market on security best practices.
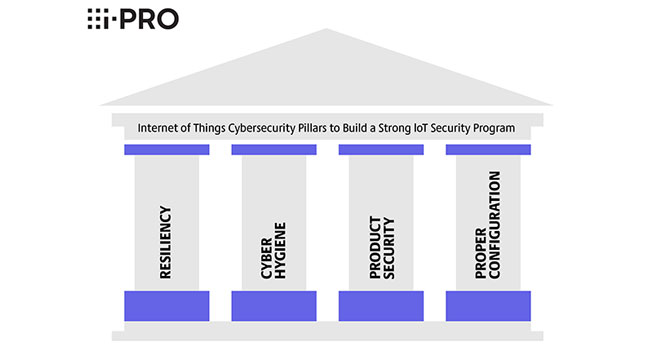
i-PRO focuses on what the company believes are the four core tenets (or pillars) that should be the foundation of any IoT security program. The four pillars are resiliency, cyber hygiene, product security, and proper configuration.
Four Pillars of Cybersecurity for IoT Devices
Resiliency
The first pillar focuses on resiliency, which simply put means that your IoT device or security system will be there when you need it the most. Will your security system work during a power outage, severe weather, communication disruption (telephone or internet outage), or cyber-attack? Questions like this will help your organization determine if your devices are resilient. One of the toughest challenges in achieving true resiliency is marrying physical security and cybersecurity together.
Cyber Hygiene
Cyber Hygiene is concerned with the care and maintenance of IoT devices. When was the last time you updated your IoT firmware or software? Do you have an inventory of all IoT devices on your network? Are you using strong passwords or authentication for your IoT devices? Did you ever change the default passwords on your IoT devices? These questions will give you a sense of your cyber hygiene. IoT devices must be updated and inventoried just like any other device on the network. Often they overlooked or forgotten about once deployed.
Product Security
Product security refers to the security features on the device itself. Many IoT devices, especially cheap ones or devices made by fly-by-night companies, do not build security features into their devices. We recommended purchasing devices from reputable companies that will fix security flaws as they are reported. Some of the security features to look for in an IoT device are encryption (protecting usernames, passwords, and device traffic), authentication (does the device ensure that it only takes instructions for an authenticated source), and the support of secure network standards like 802.1x.
Proper Configuration
While the security features of an IoT device are important, they become pointless if they are not configured or set up properly. Proper configuration focuses on ensuring the devices have the security features turned on, and turning off any features that aren’t in use, but it also includes making sure that the network is set up properly. Often these IoT devices are hacked because attackers can get to the devices in the first place, one way to help with that is by ensuring that your IoT devices are not visible from the internet. This can be done by properly configuring the network and using network security best practices such as network segmentation.
“Over the next few weeks, i-PRO will release more detailed explanations of each pillar and best practices as part of its blog series on the topic. https://i-pro.com/global/en/surveillance/news (click on Blog under News and Events)”
“Over the next few weeks, i-PRO will release more detailed explanations of each pillar and best practices as part of its blog series on the topic. https://i-pro.com/global/en/surveillance/news (click on Blog under News and Events)”