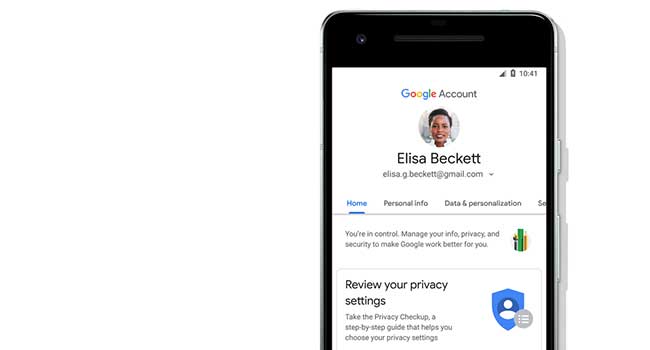
Google has announced it has overhauled it's privacy and security settings service
- By Sydny Shepard
- Jun 26, 2018

What business should do to protect against APTs
- By Brad Thies
- Jun 25, 2018

Insight into how digital learning technology will shape schools in the future
The wall-mounted version of the Security Control and Observation Tower (SCOT™) provides increased visibility to organizations at a fraction of the cost

The reputation of the “Dark Web” perhaps exceeds its reality

Make secure transactions with the best VPN service

Kicking off a cloud-first strategy without considering security measures can cloud your judgement
- By Robert Huber
- Jun 19, 2018
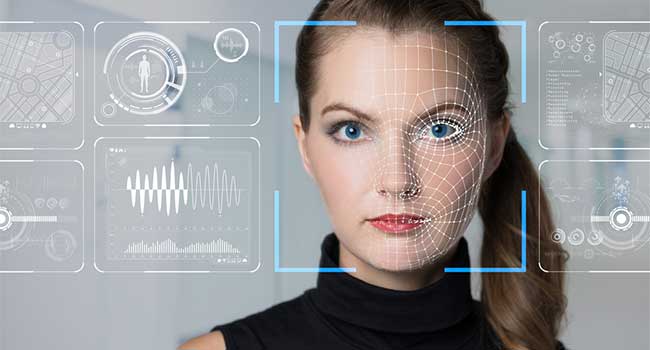
The ability of the latest developments in deep learning and neural networks to detect suspicious behaviour looks set to revolutionize security and law
- By David Fulton
- Jun 19, 2018

CBP urges all international visitors to ensure they possess the appropriate U.S. travel visa for the purpose of their visit

The strategy establishes a clear vision and concrete actions that will improve DHS’s efforts to safeguard our northern border against terrorist and criminal threats

This online 90-minute training is designed to educate startup companies and social media companies about how terrorists may seek to exploit their platforms.

Strong nosed K-9s help police sniff out electronics.
- By Sydny Shepard
- Jun 14, 2018

The impact of updates to policy and specifications for the expanded use of standards-based technologies on securing identity and access in government was a leading theme throughout the two-day event.
- By Randy Vanderhoof
- Jun 13, 2018

The city council approved $114,000 for security cameras to be installed at the parks and an additional $100,000 for park security
- By Sydny Shepard
- Jun 13, 2018
Campus Achieves Comprehensive Data Protection and Centralized Management for Entire Security and Surveillance Ecosystem with Pivot3 and Milestone Systems

Educational institutions are a data treasure trove.
- By Isaac Kohen
- Jun 12, 2018

Researchers are pairing artificial intelligence and drones in the latest experiment to prevent crimes before they happen.
- By Sydny Shepard
- Jun 11, 2018

IP security cameras are connected to the internet. That's what allows users to access them remotely, to check in on their business, and what lets manufacturers update device software without having to physically visit their business.

Four months after two students died in a shooting on campus, the district is layering security measures to keep students safe.
- By Sydny Shepard
- Jun 07, 2018

Installing alarms, safety training and fencing could be the difference in a secure farm.
- By Katie Torrance
- Jun 07, 2018
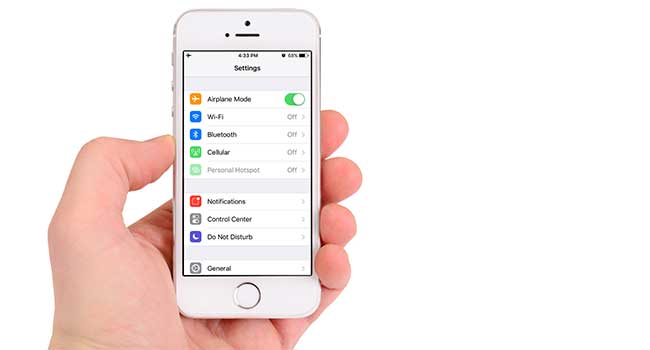
Apple has announced new settings to strengthen security on your mobile, laptop and tablet devices.
- By Sydny Shepard
- Jun 06, 2018

The Vehicle Face System is planned for testing in August at the Anzalduaz Port of Entry in Texas.
- By Sydny Shepard
- Jun 06, 2018