
Our goal of clustering attacks on web applications is two-fold
- By Gilad Yehudai
- Jul 11, 2018

Timehop disclosed a security breach that has compromised the personal data, including names and emails, of its 21 million users
- By Sydny Shepard
- Jul 10, 2018

Information Security it is one of the most in demand skill sets in all the technology industry.
- By Anthony Coggine
- Jul 06, 2018

This new AI could present new challenges as well as opportunities
- By Harold Kilpatrick
- Jun 29, 2018

\Wi-Fi Alliance is looking to beef up security with an updated protocol
- By Sydny Shepard
- Jun 27, 2018
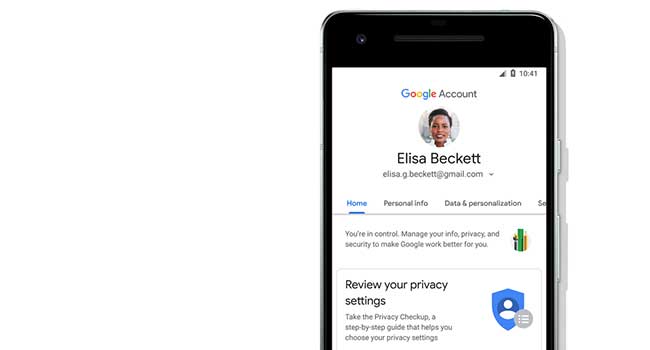
Google has announced it has overhauled it's privacy and security settings service
- By Sydny Shepard
- Jun 26, 2018

What business should do to protect against APTs
- By Brad Thies
- Jun 25, 2018

Insight into how digital learning technology will shape schools in the future

The reputation of the “Dark Web” perhaps exceeds its reality

Make secure transactions with the best VPN service

Kicking off a cloud-first strategy without considering security measures can cloud your judgement
- By Robert Huber
- Jun 19, 2018

This online 90-minute training is designed to educate startup companies and social media companies about how terrorists may seek to exploit their platforms.

Educational institutions are a data treasure trove.
- By Isaac Kohen
- Jun 12, 2018

IP security cameras are connected to the internet. That's what allows users to access them remotely, to check in on their business, and what lets manufacturers update device software without having to physically visit their business.
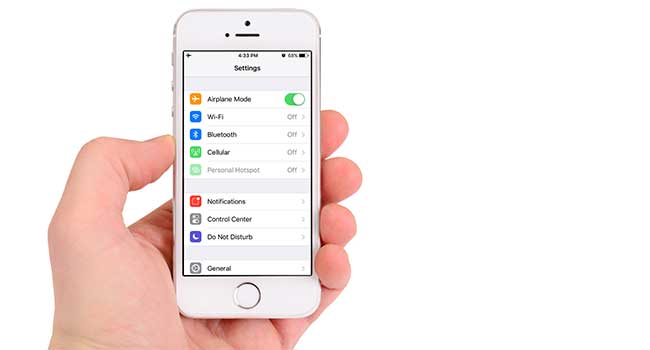
Apple has announced new settings to strengthen security on your mobile, laptop and tablet devices.
- By Sydny Shepard
- Jun 06, 2018

Several companies are opting for short-term reactive cybersecurity despite high profile ransomeware attacks.
- By Sydny Shepard
- Jun 05, 2018

Over the last decade, the cloud has revolutionized the way businesses operate. Today, modern enterprises are turning to a hybrid IT environment, leveraging the best of both worlds—the scalability of cloud infrastructure and the control of on-premises systems.
- By David Meltzer
- Jun 01, 2018

Researchers find nearly half a million routers have been infected by malware.
- By Sydny Shepard
- May 29, 2018

If your business has customers who live in the European Union, you have an important deadline approaching.
- By Jay Hamilton
- May 21, 2018

A report by Verizon has found that 76 percent of breaches are financially motivated, and 68 percent of those breaches took months or longer to discover.
- By Sydny Shepard
- May 17, 2018