Acoem, a provider of advanced acoustic threat detection solutions, today announced the appointment of Edwin (Ed) Brennen as Business Development Manager for its ATD (Acoustic Threat Detection) team. With more than 35 years of experience across public sector technology and electronic security, Brennen will lead Acoem’s channel partner development efforts in North America.

Four people were killed, including a NYPD officer, in a midtown Manhattan shooting on Monday. That’s according to CNN.
- By Brent Dirks
- Jul 29, 2025

Biometrics applications for security, workplace time clocks, and access control authentication have advanced rapidly, especially over the past 25 years. Innovations in facial identification have made some of the most dramatic recent strides.
Once limited to large corporate and government sites that required the highest level of security and could justify the cost, biometric technology has become much more practical, affordable, and trustworthy for an increasingly wider array of useful and important purposes.
- By Albert Nissimoff
- Jul 29, 2025

Artisan Apartment Homes, a luxury apartment complex in Dunedin, Florida, recently transitioned from mechanical keys to electronic locks and centralized system software with support from Allegion US, a leading provider of security solutions, technology and services, and Florida-based Comfort Technologies, which specializes in deploying multifamily access control, IoT devices and software management solutions.

Mall of America®, the largest shopping and entertainment complex in North America, announced an expansion of its ongoing partnership with Axis Communications to deploy cutting-edge car-counting video analytics across more than a dozen locations. With this expansion, Mall of America (MOA) has boosted operational efficiency, improved safety and security, and enabled more informed decision-making around employee scheduling and streamlining transportation for large events.

An advanced, end-to-end video solution from IDIS, with a focus on reducing waste and costs, has helped a major office development in the City of London align its security with sustainability objectives.

Motorola Solutions has today been named the Official Safety Technology Supplier of the 2025 and 2027 Ryder Cup, professional golf’s renowned biennial team competition between the United States and Europe.
CENTEGIX, a leader in wearable duress badges, today announced it has been named an Industry Partner by the Texas Hospital Association (THA), a designation that streamlines access to vetted, high-impact solutions for hospitals and healthcare systems across Texas.

In today's rapidly evolving security landscape, the convergence of on-prem, edge and cloud technologies are critical. The physical security landscape is undergoing a profound transformation, driven by the rapid digitalization of buildings and the evolving needs of modern organizations. As the buildings sector pivots towards smart, AI and data-driven operations, the integration of both edge and cloud technology has become crucial.
- By Emma Falck
- May 20, 2025

Despite the proliferation of constantly evolving security solutions, there remains a troubling trend among many facility operators who often neglect the most important security assets within their organization. Keys and shared devices like radios, laptops and tablets are crucial to successful operations, yet many operators are managing them haphazardly through outdated storage systems like pegboards and notebooks.
- By Craig Newell
- May 16, 2025
Omnilert has announced that Amerant Bank has chosen Omnilert’s AI technology to help bolster the security at all of its locations in Florida.

The first initiative as partners included a joint fundraising campaign to enhance school safety, generating $42,000 for Safe and Sound Schools programs.

The Cybersecurity and Infrastructure Security Agency (CISA) states “There are 16 critical infrastructure sectors whose assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, and national public health or safety or any combination thereof.”
- By S. Guerry Bruner
- Mar 03, 2025

i-PRO Co., Ltd.,(formerly Panasonic Security), a manufacturer of edge computing cameras for security and public safety, recently announced that a leading teaching hospital in Northeast England, has enhanced its security infrastructure with i-PRO X-Series cameras integrated with Milestone’s XProtect Video Management Software (VMS).
The National Center for Spectator Sports Safety and Security (NCS⁴) at The University of Southern Mississippi (USM) hosted the National Intercollegiate Athletics Safety and Security Forum at Duke University Jan. 28-29. More than 150 safety and security professionals from across the country representing all areas of Intercollegiate Athletics attended the sold-out Forum.
Interface Systems, a managed service provider of security, actionable insights, and purpose-built networks for multi-location businesses, today announced that Nicker Management, a fast-food franchise operator in the Los Angeles area, has successfully implemented Interface’s Virtual Security Guard solution. By deploying Interface’s advanced security technology, Nicker Management has enhanced safety, reduced operational costs, and provided a secure environment for employees and customers.
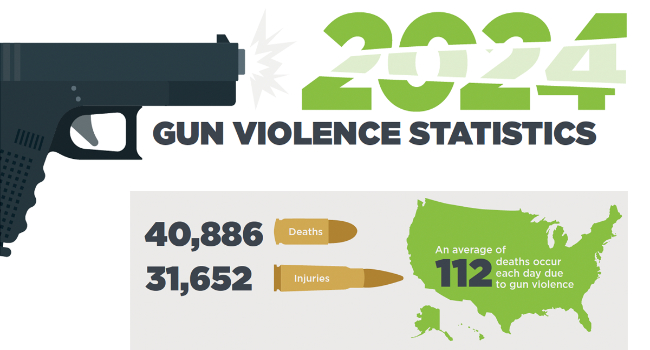
Omnilert, provider of gun detection technology, today released its compilation of Gun Violence Statistics for 2024 summarizing gun violence tragedies and their adverse effects on Americans and the economy. While research showed a decrease in overall deaths and injuries, the rising number of school shootings and fatalities and high number of mass shootings underscored the need to keep more people safe in schools as well as places of worship, healthcare, government, retail and commerce, finance and banking, hospitality and other public places.

Axis Communications, provider of video surveillance and network devices, today announced the implementation of a custom surveillance solution developed in collaboration with the MetLife Stadium security team. This new, tailored solution will help the venue augment its security capabilities, providing high-quality video at unprecedented distances and allowing the security team to identify details from anywhere in the venue.

Overseeing the use of generative artificial intelligence, enhancing cybersecurity and ensuring compliance with a host of federal healthcare regulations headline the Top Risks health systems face in 2025, according to an annual study by Kodiak Solutions.
Interface Systems, a leading managed service provider of business security, actionable insights, and purpose-built networks for multi-location businesses, today announced the successful deployment of its Virtual Security Guard solution for Madan-Russo Organization. The family-owned owner-operator of a global fast-food chain in northern New Jersey has significantly improved safety and reduced security costs by up to $12,000 monthly at one of its most at-risk locations.