
To combat persistent retail crime and deliver peace of mind to workers in the bustling North Leroy Street business district, the City of Fenton Police Department has deployed a new AI-powered video surveillance system with camera-sharing technology to accelerate response time during retail heists or other emergencies.

During 2024, the Transportation Security Administration (TSA) intercepted a total of 6,678 firearms at airport security checkpoints, preventing them from getting into the secure areas of the airport and onboard aircraft. Approximately 94% of these firearms were loaded. This total is a minor decrease from the 6,737 firearms stopped in 2023. Throughout 2024, TSA managed its “Prepare, Pack, Declare” public awareness campaign to explain the steps for safely traveling with a firearm.
NAPCO Security Technologies, Inc., based in Amityville, NY, is proud to announce Peter Lowenstein’s promotion to head up sales for Napco Access, a newly unified group combining the company’s three access control divisions: Alarm Lock, Marks USA, and Napco Access Pro (formerly Continental).

A new survey from Pro-Vigil looks at video surveillance trends, how AI is impacting physical security, and more.
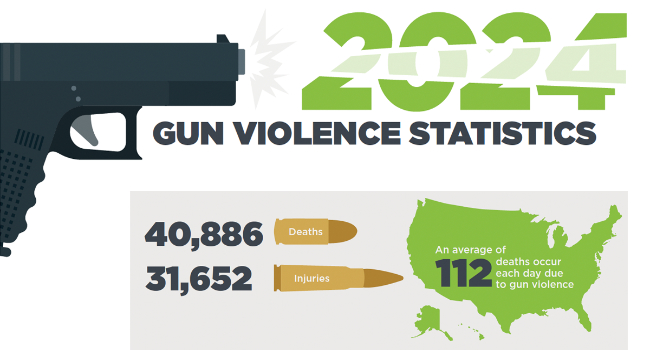
Omnilert, provider of gun detection technology, today released its compilation of Gun Violence Statistics for 2024 summarizing gun violence tragedies and their adverse effects on Americans and the economy. While research showed a decrease in overall deaths and injuries, the rising number of school shootings and fatalities and high number of mass shootings underscored the need to keep more people safe in schools as well as places of worship, healthcare, government, retail and commerce, finance and banking, hospitality and other public places.
As residential and commercial surveillance technology continues to advance, Snap One, now part of ADI, is evolving and investing in Luma by adding a new line of Luma 4K Hybrid cameras that deliver enhanced performance features and versatile designs.

Axis Communications, provider of video surveillance and network devices, today announced the implementation of a custom surveillance solution developed in collaboration with the MetLife Stadium security team. This new, tailored solution will help the venue augment its security capabilities, providing high-quality video at unprecedented distances and allowing the security team to identify details from anywhere in the venue.
Per Mar Security Services, a provider of total security solutions based in Davenport, Iowa, has acquired Accu-Com Security Solutions, an Oshkosh, Wisconsin-based company specializing in burglar, fire, video, and access control systems.
As the physical security industry looks toward 2025, i-PRO Co., Ltd. (formerly Panasonic Security) is highlighting four interlinked trends that are set to redefine how businesses, integrators, and security professionals approach security in the next year. These insights highlight the transformative role of edge computing, artificial intelligence (AI), the expansion of cloud computing, and how companies will integrate the wealth of available data.
RapidFire Safety & Security (RapidFire), the multi-regional “Buy & Build” experts for fire, life safety, and security industries, announced the acquisition of Kane Fire Protection (Kane) in the St. Louis, Metropolitan area. The acquisition of Kane Fire Protection expands RapidFire’s service offerings with the addition of Kane’s fire sprinkler services. This represents RapidFire’s second acquisition in the St. Louis market, where they are also headquartered.
The Security Executive Council (SEC) is partnering with the Strategic Consortium of Intelligence Professionals (SCIP) to further a shared mission of providing resources and thought leadership to the private-sector intelligence community.
Mission 500, the security industry's nonprofit charity dedicated to supporting children in need across the US, Canada, and Puerto Rico, is pleased to announce several key updates to its Board of Directors. Jason Lutz, previously Treasurer, has been named Chair, succeeding Co-Chairs Tracy Larson and Janet Fenner. Board member John Nemerofsky is named Treasurer, and Garrett Savage, Secretary, succeeding Sarah Flanagan.

The White House recently announced the launch of a cybersecurity label for internet-connected devices, known as the U.S. Cyber Trust Mark, completing public notice and input over the last 18 months. During that time, FCC Commissioners decided in a bipartisan and unanimous vote to authorize the program and adopt final rules, as well as the trademarked, distinct shield logo that will be applied to products certified for the U.S. Cyber Trust Mark label.

Motorola Solutions has entered into a definitive agreement to acquire Theatro Labs, Inc., maker of AI and voice-powered communication and digital workflow software for frontline workers, based in Richardson, Texas.
Napco Access Pro, a division of NAPCO Security Technologies, is pleased to announce its CA4K Enterprise Security/Access Control/Video Platform, having undergone rigorous testing and evaluation, is now FIPS 201 Approved, using the FIPSlink Validation Client validation system from IdentityOne.
- By Ralph C. Jensen
- Jan 07, 2025
G4S recently announced the appointment of Michael Leahey to the position of chief financial officer. Leahey joins G4S from parent company Allied Universal®, where he served as vice president of corporate finance. Leahey will report to Tim Brandt, Allied Universal’s global chief financial officer and Ashley Almanza, executive chairman of G4S/Allied Universal International.
Acre Security, a global leader in providing cutting-edge security platforms, is proud to announce the acquisition of REKS, a transformative purpose-built, generative AI solution designed for access control environments. This strategic deal marks a significant step forward in Acre’s mission to drive innovation and redefine the future of security technology.

The Foundation for Advancing Security Talent (FAST) has announced the third annual National Security Technician Day, an annual commemorative day held on Jan. 23 to honor security technicians across the country.