
ASSA ABLOY has signed an agreement to acquire August Home, a leading smart lock business in the US.

Florida Governor Rick Scott has declared a state of emergency for the event.
- By Sydny Shepard
- Oct 19, 2017
Radeed Prince killed three and injured two more in Edgewood, Maryland and injured one more in Wilmington, Delaware.
- By Sydny Shepard
- Oct 18, 2017

Construction crews broke ground two weeks ago to build eight prototypes for the Trump Administration's Border Wall.
- By Sydny Shepard
- Oct 18, 2017
DHS will issue a "binding directive" which will require the implementaion of security measures for email.
- By Sydny Shepard
- Oct 18, 2017

A University of Kansas student was able to use a keystroke logger to gain access to a professor's computers and change his grades.
- By Sydny Shepard
- Oct 17, 2017

Attacks on Christmas markets and festivals in 2016 have motivated officials to boost security in order to prevent mass-casualty attacks.
- By Sydny Shepard
- Oct 17, 2017

The hole in Wi-Fi security affects the vast majority of Wi-Fi devices and networks.
- By Sydny Shepard
- Oct 16, 2017

Oops!...Equifax did it again.
- By Chris Olson
- Oct 16, 2017
Total Recall Corporation, a Convergint Technologies Company, will showcase its latest CrimeEye citywide video surveillance solutions.
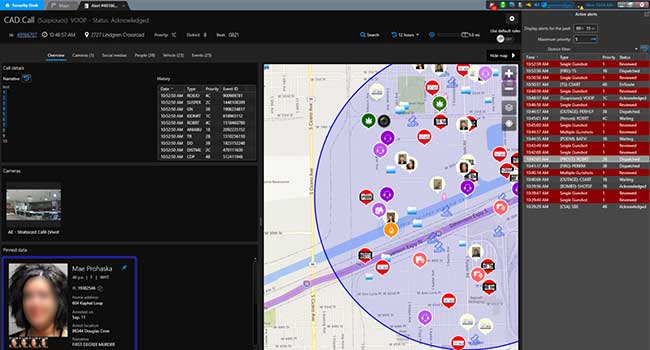
Genetec Inc. announced the launch of its new public safety decision support system, Genetec Citigraf. Created for citywide law enforcement and public safety agencies.

The certification would give the stadium legal protections in the event of a terrorist attack.
- By Sydny Shepard
- Oct 13, 2017
The University offers an array of technical and standards-based information for contractors, integrators, end users and consultants.
Delta Turnstiles announced the second model in its Designer Series of turnstiles - the Sunrise.

According to a new study, 70 percent of employees cannot grasp web security and privacy.
- By Sydny Shepard
- Oct 12, 2017
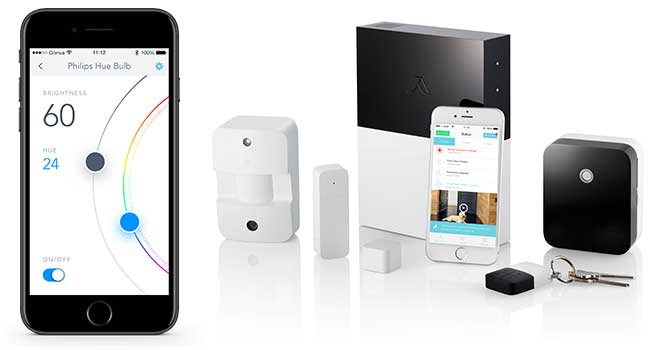
abode Systems' is expanding features to allow users to build a smart home their own way.
- By Sydny Shepard
- Oct 12, 2017

Dubai International Airport is replacing security checks with an aquarium. Yes, you read that right.
- By Sydny Shepard
- Oct 11, 2017

The new Arlo Pro 2 includes HD Video, option 24/7 continuous video recording and a solar power option.
- By Sydny Shepard
- Oct 11, 2017