
November/December 2019
- Security Foresights for the New Year
- The Security of Medicine
- Looking to the Future
- Integrated Technology Drives Security
- Reshaping the Perimeter
Cover Story

By Ralph C. Jensen
In keeping with SwedishAmerican’s mission to deliver excellence in healthcare, they also maintain the highest level of care when it comes to keeping their patients, medical staff, and facilities safe.
Features
By Ronnie Pennington
Today’s professional security industry seems to have adopted the “more power” mantra by taking a much more pragmatic approach.
By Craig Summers
Driven by the 2013 physical assault on a California substation, the NERC CIP 14 regulation has reshaped the way energy’s physical security directors are viewing perimeter security.
By Tom Galvin
As we wind down 2019 and look forward to a new decade, it is time to reflect upon the year and the megatrends that have started to influence video surveillance and the physical security industry.

By Valerie Anderson
Most security professionals would agree the rapidly-evolving nature of technology can be daunting, not only for end users but also for systems integrators and consultants alike.
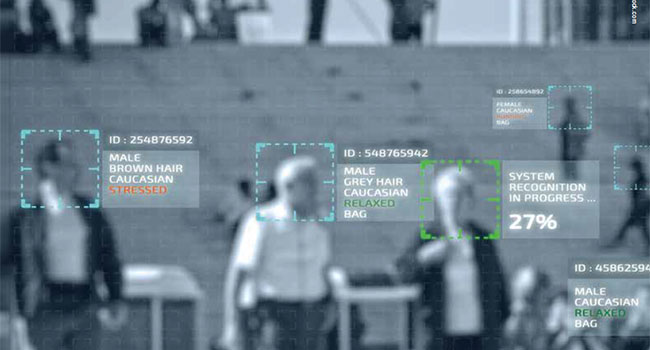
By Brian Carle
Video surveillance technologies continue to evolve. Some of the fastest-growing areas include AI-based video analytics and cloudbased video access and recording.

By Fredrik Nilsson
You have probably heard the old adage, “Hindsight is always 20/20.” Looking forward though, our vision is not nearly as clear.

By Clayton Brown
Once upon a time, this was the year when cars could fly, human immune systems healed themselves and cops could stop a crime dead in its tracks. While some of these things are still more of a dream than a reality, the last one is becoming more viable every day.

By Laura Fradette
It is hard to believe that 2019 is coming to a close. As we look ahead to the New Year, sitting with colleagues, we reflected on the trends that impacted our industry in 2019, and predict what we can look forward to in 2020 and beyond.
Departments
INDUSTRY PROFESSIONAL
By Sherelle Black
The way people and businesses communicate is ever evolving, and with that, so are the communication products.
INDUSTRY FOCUS
By Ralph C. Jensen
It would seem everyone has a crystal ball when it comes to forecasting the future. What I have discovered is that some crystal balls are a little more polished than others. I’m pleased to have several contributors who will give us all some incredible insight into 2020.
Networking Security
By Jorge Del Prado Lera
This evolution not only keeps the IT department in a constant state of change, but also dramatically changes the way the overall business must adapt to stay competitive.
By Felicia Haggarty
Not only does modern software architecture create a broader attack surface area, the accelerated DevOps methodology makes it harder to detect and remediate vulnerabilities.