
Gaining Intelligence
As biometrics authentication technology proliferates, it leaves fingerprints on many sectors of society
- By Milind Borkar
- Mar 01, 2013
 Over the past decade, we’ve witnessed a shift from identity authentication based on signatures, PINs and identification cards, which can be easily lost or stolen, to biometrics-based identity authentication.
Over the past decade, we’ve witnessed a shift from identity authentication based on signatures, PINs and identification cards, which can be easily lost or stolen, to biometrics-based identity authentication.
How does this impact the future of identity authentication? Imagine walking through airport security without waiting in line, or being able to quickly and securely get money from an ATM without having to remember a PIN. Imagine accessing your workplace without using an identification or access card. These innovations are quickly becoming realities as our world shifts from using access cards and PINs to the new digital age of secure identification and access control based on biometrics.
Today’s biometrics systems are moving identity authentication toward realtime, accurate and secure individual ID based on unique biometric characteristics, including iris patterns, fingerprint minutiae, facial structure or voice. A biometric identification system is able to quickly recognize and analyze these anatomical traits, match them against a database of templates and either grant or deny access to information or a location.
Architecture of Biometrics Systems
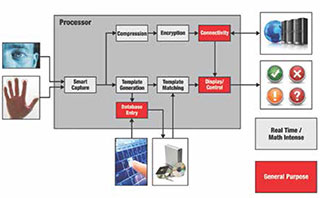
While biometrics systems range in their performance, power consumption and peripheral integration, the basic architectures of all systems is similar because the functions they must perform are similar. Biometrics systems typically manage sensing, feature extraction, template matching and decision output processes.
Sensing. The sensing component—often a camera, CMOS, CCD or optical sensor—captures the subject’s biometric characteristic, inputs it into the system, and converts the analog data into digital information.
Feature extraction. During this step, the processor takes information from the sensor and extracts data points to construct a template, or model, of the subject’s biometric characteristics. The algorithms that enable the processor to extract the features, such as segmentation, grey stretch, block direction and Gabor filtering, can be computationally intense and place high demands on the systems’ processing capabilities. Digital signal processors (DSPs), with their math optimized architecture, are ideal for feature extraction in biometrics applications.
Template matching. In this process, the system compares the newly generated biometric template with those stored in a database of people who are allowed access. If the template does not match an approved template in the database, the person is not granted access. To enable quick access, the processor architecture must perform high-speed template matching and quickly pass its decision onto the output device to allow or deny access within seconds.
Distributing a biometric system’s processing load across a computationally powerful DSP and a general purpose processor (GPP) platform can increase the processing efficiency, allowing for the deployment of less costly processing platforms or providing the added processing capabilities needed for more sophisticated biometric algorithms. Texas Instruments develops a variety of solutions that can address these needs.
Biometrics Today
Biometric authentication technology has significantly advanced over the last decade as the necessary computational abilities, power consumption and cost effectiveness of digital signal processing have become more sophisticated. Developers are able to integrate faster and more cost-effective processors into their systems and implement more sophisticated algorithms, all while reducing the price of their systems.
Over the next few years, biometrics technology will become even more pervasive in our everyday lives. Biometric passports have already been adopted by many countries, including the United States, the United Kingdom and other European countries. These systems match the passport owner’s face against a digital template of their face that is stored in the passport.
In addition, the Department of Homeland Security has instituted the Visitor and Immigration Status Indicator Technology (US-VISIT) program to collect digital fingerprints and facial images of international visitors to the United States, ensuring proper biometric identification at the border. The database is shared among numerous governmental agencies. The FBI also manages its own Biometric Center of Excellence.
India, one of the most populous countries in the world, is undertaking a Unique Identification Number (UID) program to enroll all of its citizens in a biometric identity database. More than half of India’s 1.2 billion citizens are expected to be enrolled by 2014. With 20,000 enrollment sites across the country, India adds about one million biometric identities every day. The UID program is aimed at improving the government’s distribution of about $60 billion in welfare support to India’s poor and rural areas, where residents do not have proper identity documentation and have difficultly opening bank accounts.
Biometric systems input and store information on all 10 fingerprints and both irises, and take a digital photograph of the face. India’s nationwide program will certainly offer lessons to the rest of the world regarding how to implement a largescale biometric authentication program that can be trusted by the population.
“Soft biometrics” systems have recently been developed, not to authenticate the exact identity of individuals, but to identify their general demographics, including gender and age. Retail locations are using this information to target their digital advertising toward different demographic groups.
Biometrics in the Future
In the coming years, the selection of processing elements on which to base biometrics systems and safeguards for biometric databases will become even more sophisticated. Systems also will evolve into smaller form factors, including more battery-powered handheld authentication devices.
One place we expect to see biometrics applications grow in the near future is point-of-sale systems. This will be a more convenient way to pay for purchases, while making identities more difficult to steal and keeping financial information safer.
This article originally appeared in the March 2013 issue of Security Today.