
Security System Advantages
Internet links everything from commerce to courting
- By Chuck Westfall
- Mar 01, 2013
 The Internet has revolutionized everything from commerce to courtship for billions of people around the world. It is no surprise, then, that the growth of high-speed IP networking also has impacted the video security industry, making surveillance systems more flexible and efficient than ever before.
The Internet has revolutionized everything from commerce to courtship for billions of people around the world. It is no surprise, then, that the growth of high-speed IP networking also has impacted the video security industry, making surveillance systems more flexible and efficient than ever before.
System design and equipment choices designed to protect key assets—personnel, physical plants and merchandise—have never been more diverse. Although analog video systems may still seem appealing for smaller installations because of their comparatively lower cost, IP-based systems offer many advantages for capturing and transmitting high-quality HD images via the Internet or a LAN connection for remote monitoring. IP video cameras tend to be simple to install, thanks to such features as PoE and the widespread nature of IP networks, which make additional cabling unnecessary.
Compact digital IP cameras can zoom-in on surrounding environments to provide comprehensive observation of sensitive areas. Some cameras even provide remote-controlled robotic pan and tilt. Industry standards, such as the Open Network Video Interface Forum (ONVIF) Profile S, provide compatibility among different security products used in IP video security networks.
The ability to view, save and transfer video digitally via an Ethernet network that can provide a full megapixel feed for viewing and/or recording at a central monitoring location—or a more compressed stream of the same video on a password- accessed smart phone or iPad—leads to unprecedented convenience and efficiency. Video can be recorded, shared and transmitted over long distances, eliminating the barriers of physical distance. Rather than debate the relative merits of analog and digital, let’s concentrate on the benefits of networked digital IP-based video security systems. This market is growing substantially, thanks in no small part to the IP security camera manufacturers that have worked tirelessly to find ways of improving performance while controlling costs.
Network Imaging
Digital computer technologies have revolutionized every form of imaging, whether it’s at the local movie theater or on the surface of Mars. In IP security cameras, the benefits of computer technology start with the lens, which must be precisiondesigned and manufactured to produce crystal-clear, low-distortion images from corner to corner in conditions ranging from extremely low light to extremely highcontrast lighting. This is especially true if the lens is designed to be integral to the camera and provide special features, such as a wide angle of view or a 20x or 40x zoom to capture crucial visual details at a distance.
These performance capabilities require supercomputer optical design, and those IP security camera manufacturers with the in-house expertise to achieve them are a step ahead of competitors who must purchase lenses from outside suppliers. Inhouse design and manufacturing ensures better performance because lenses can be built to work in total synergy with other key camera components, such as image sensors, digital network video processors and image processors.
Recent advances in CMOS image sensor technology have made them more economical than ever to offer megapixel IP security cameras, which provide approximately four times the pixel count and twice the linear resolution of conventional VGA cameras. Today’s quality HD megapixel IP security cameras also include a digital network video processor—a powerful, highly efficient compression, encryption and transmission engine. Advances in the digital compression algorithms employed by these processors have resulted in more efficient data storage with minimal loss of image quality. These new algorithms enable users to manage the increased volume of image data produced by HD megapixel IP security cameras more effectively.
A good-quality megapixel IP security camera offers multiple resolution and data compression options to suit the needs of diverse users, who may wish to view security images on any number of contemporary digital display devices. In addition to megapixel resolution for detailed image analysis on a large monitor, many users require VGA resolution for low-cost monitor display, and QVGA (320 x 240) or even QQVGA (160 x 120) resolution for use on mobile devices such as smartphones.
The two dominant forms of data compression in modern IP security cameras are Motion JPEG and MPEG-4 or its subset, H.264. Motion JPEG is best for applications where there is a need to extract individual video frames for detailed analysis, while MPEG-4 offers superior data compression for video data storage. The better megapixel IP security cameras on the market today provide simultaneous output of Motion JPEG at a variety of resolutions and MPEG-4 or H.264 video.
Additional digital image processors in today’s megapixel IP security cameras can be designed to optimize picture quality in a variety of ways, ranging from the preservation of detail with a simultaneous reduction of noise—even in low-light— to the accurate rendering of colors and tones. Megapixel IP security cameras can achieve excellent quality in color at light levels as low as .03 lux. For black-and-white images, good quality has been achieved at light levels as low as .001 lux, and for high-contrast lighting conditions, new algorithms can allow selective brightening of shadow areas in the image without the loss of detail in brightly lit areas.
This capability is invaluable for many environments that combine outdoor/ indoor illumination in a single scene. Added together, digital processing for low-light/low-noise imaging and color accuracy combined with precision optics, and HD megapixel resolution video that can be viewed and/or recorded via any Internet connection amounts to a formidable security tool. But the advantages of an IP video security camera systems don’t end there.
Video Analytics
The large amount of monitored video from IP cameras observing sensitive locations is a challenge for today’s security professionals at all levels. Fortunately, automated video analysis, using computer intelligence to detect crucial details that might elude human observers, is now a built-in feature in many megapixel IP security cameras. Known as video analytics, this innovation increases the information value of security video and can benefit the ROI in monitoring staff and equipment, and improve the efficiency and overall bottom line of security organizations.
Video analytics can be as basic as the capability of some PTZ IP video cameras to automatically identify and track motion within a scene—based on useradjustable settings—to more advanced features that make the camera, in effect, a “partner” in detecting anomalous events. These intelligent features can include the detection of abandoned, moving or removed objects in an image, combined with the triggering of an alert signal when such events occur.
Examples of situations where video analytics in action include detecting abandoned briefcases or backpacks in public areas (airports or other transportation centers), movement in areas where there shouldn’t be any (a retail store), the absence of an object that should ordinarily be in a picture (artwork in a museum), or “tripwire” intrusion past a user-preset line or object and into restricted areas (a doorway, window, driveway or other boundary).
Video analytics can be user-adjustable in terms of detection area—automatically highlighted for instant visual identification—sensitivity and duration. Video analytics also gives users the option to economize on video archiving, since they differentiate between important video segments from those that are not.
Reinforcing video analytics are camera analytics, which can include the detection of abnormal noises in the camera’s immediate vicinity, ranging from the sound of gunshots to someone tampering with the camera or physically abusing it. Physical disturbances to the camera and its protective dome also can trigger alerts. Additional video analytics can be provided by computerbased recording hardware programmed to recognize faces, shapes, objects and other user-determined details.
Mindful of privacy concerns, some manufacturers of IP video cameras offer users the ability to create a privacy mask to block the view of sensitive locations, such as residential doors and windows, ATM keypads or computer monitors. User-settable, privacy masks are especially convenient for large installations of IP video security cameras in urban areas, where there may be a mix of commercial properties needing scrutiny and private residences that do not. Advanced digital control of IP video security cameras can provide major benefits to installers, especially where large numbers of cameras are involved.
Remote Adjustment
Because each IP video security camera has its own IP address, it can be viewed individually. Users can even set-up firewall access to secure and encrypt the data flow to and from the camera. Better-quality cameras further leverage this authorized-user addressability with remote-adjustment features that can save installers and end-users major expense in adjusting or re-setting the image-capture area and focus settings of large numbers of stationary cameras, and/or cameras that are particularly inaccessible.
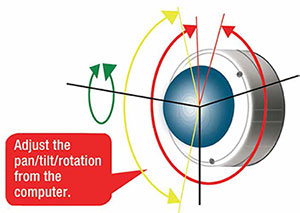
Using a software application running on any Internet-connected PC, the best IP security cameras let you remotely disconnect the camera from its VMS and then adjust its PTZ, rotation and focus settings. Doing this from your desktop is less costly and easier than having a technician climb a ladder or use a bucket truck to access multiple cameras, remove each camera’s dome cover and then putting it all back together again.
When choosing an IP video camera, it’s important to make sure it provides four-axis remote control of PTZ, rotation and focus settings. That fourth axis makes a critical difference because it enables you to adjust the horizon of the camera once you’ve achieved a new field of view.
This article originally appeared in the March 2013 issue of Security Today.