
Internet Explorer Browser Security Tips
Don't become the next Internet victim!
- By Ginger Hill
- Mar 20, 2013
From lurking spyware to sophisticated hackers, you need to build a line of defense to help ensure safe Internet browsing. Consider the following tips to establish your safe browsing plan with Internet Explorer.
1. Use Internet Explorer's private browsing mode. Not only will this feature leave no traces of your browsing history, but it is also useful when checking your email on any other device besides your own because no cookies are recorded.
Quick How-to: Press Ctrl + Shift + P all at the same time to enable this mode.
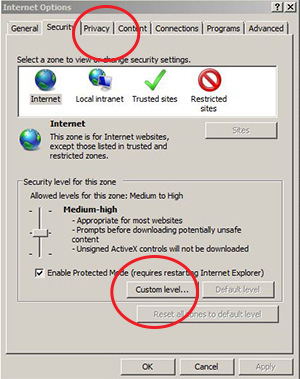
2. Select the appropriate security zone on Internet Explorer. All websites start out in the "Internet zone," and it is recommended to apply the "high" security setting, disabling ActiveX, Active scripting and Java, making IE more secure.
Quick How-to: Tools → Internet Options → Security Tab → Custom Level → Click Default Level and drag slider to "High"
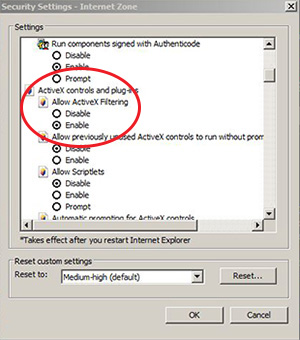
3. If needed, manually disable ActiveX controls. Decide on a site-by-site basis whether you should enable or disable these controls. Cybercriminals have developed their own ActiveX controls to damage your computer, if you visit a web page that contains malicious ActiveX software.
Quick How-to: Tools → Internet Options → Security Tab → Custom Level → Disable the "Run ActiveX controls and plug-ins."
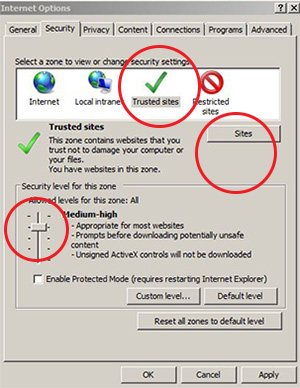
4. Add "trusted site zone" to IE for all sites that you deem safe. If you think a site has proper security without malicious content, issue it the "trusted site zone" tag. It is recommended to set the security level for "trusted site zones" to "medium-high."
Quick How-to: Tools → Internet Options → Security Tab → Click "Sites" button → Slide bar to "medium-high" position.
*Note: Remember, you can always add or remove sites from this zone as well as require that only verified sites (HTTPS) be included in this zone.
5. Unless you're supporting the Girl Scouts, block cookies. Cookies can contain any data that a website wants to store and is often used to track your computer as you move through a website, storing your preferences and credentials.
Quick How-to: Tools → Internet Options → Select Privacy Tab → Click the "Settings" button →
The following screen will appear after you click the "Settings" button. Under "Blocking "Level" set it to "High: Block all pop-ups"
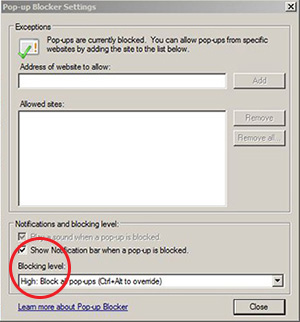
*Note: Session cookies have less risk than persistent cookies, so you can enable "always allow session cookies."
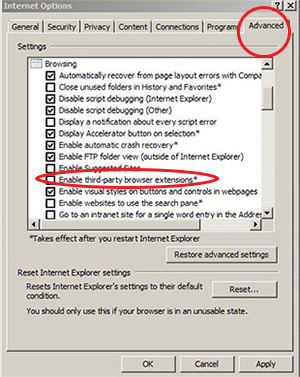
6. Disable third party browser add-ons or extensions on Internet Explorer. Some add-ons can be useful, but they have the ability to violate your privacy by monitoring your web browsing habits or changing the contents of a web page to gather your personal information.
Quick How-to: Tools → Internet Options → Select "advanced" button → Disable the "enable third-party browser extensions" option
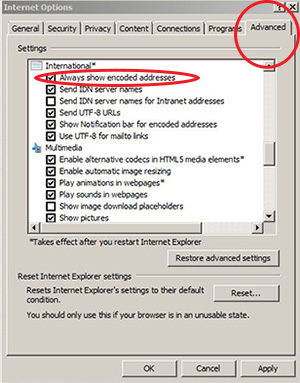
7. Protect against phishing attacks by preventing spoofing of Internationalized Domain Names (IDN). Always allow Internet Explorer to show encoded addresses, displaying IDN addresses in an encoded format helps to remove the visual similarity to the phishing domain name.
Quick How-to: Tools → Internet Options → Select "advanced" button → Enable "always show encoded addresses"
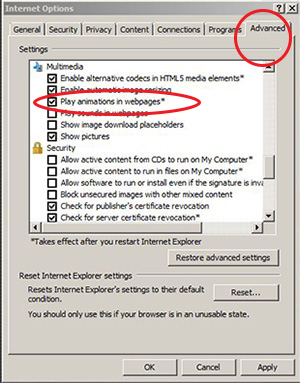
8. Allow Internet Explorer to safely deal with embedded sounds without interrupting Adobe Flash or Apple QuickTime. Web pages that have sounds may introduce security risks by having IE process additional untrusted data. It is recommended to disable the "play sounds in webpages" option.
Quick How-to: Tools → Internet Options → Select "advanced" button → Disable "play sounds in webpages"
9. Keep Internet Explorer software up-to-date. New patches are often released to repair existing vulnerabilities in the software. Remember to also keep operating system software and all other software up-to-date.