Company diligently fighting deceptive sales practices in the security industry

The decision to add metal detectors to a municipal building in Marrietta, Ga. is getting moved forward following the Virginia Beach mass shooting.
- By Sydny Shepard
- Jun 04, 2019

Quest Diagnostics has warned its 12 million customers that their personal, financial and medical data may have been exposed.
- By Sydny Shepard
- Jun 04, 2019
Polaris Private Equity Fund IV, L.P., etc., managed by Polaris Capital Group Inc. have recently agreed to a strategic capital alliance with Panasonic Corp. to acquire 80 percent of the outstanding shares of the company to be newly established by Panasonic to succeed the Security Systems Business.
- By Ralph C. Jensen
- Jun 03, 2019

The shooting, which took place in a municipal building in Virginia Beach on Friday, is now the deadliest mass shooting this year.
- By Sydny Shepard
- Jun 03, 2019
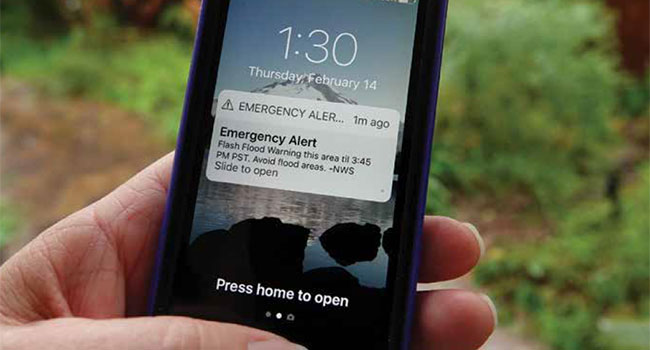
For decades, public alerting systems have served as a critical notification tool for sending alerts to citizens’ smartphones, landlines and through broadcast channels.
- By Troy Harper
- Jun 01, 2019

In recent years, however, King City has become known for a different reason; in both 2013 and 2015, the city’s homicide per capita rate for victims between 18 and 22 years of age was the highest in the state of California. The main reason for this is that the city had become a point of contention in a turf war between rival Latino gangs to the north and south of King City.

The endlessly growing mountains of personal, private data collected as part of routine transactions in our digital world continue to be a target for cybercriminals, who are moving beyond digital theft to the real world by targeting the servers that contain this data.

As you walk into a venue to cheer on your favorite team, or see a favorite singer or show, it’s likely that one of the last things on your mind is the potential for a cyber attack.
- By Chris Calvert
- Jun 01, 2019
I suppose when the topic of government security comes up, we often think big, as in the federal government. Let’s back it down a little bit and think of King City, Calif.
- By Ralph C. Jensen
- Jun 01, 2019

Multi-tenant buildings come in a variety of shapes and sizes, from a few to dozens of stories tall. Tenants may include residents, professional service providers, commercial businesses, government agencies or retail shops.
- By Dana Pruiett
- Jun 01, 2019
Just a few months ago, the Intergovernmental Panel on Climate Change (IPCC) issued its special report on the impact of climate change.
- By Julian Weinberger
- Jun 01, 2019
Although IP-based network cameras are the prevailing standard for new installations, it wasn’t that long ago that analog cameras, and the complex infrastructures required to support large numbers of them, were the only way to accomplish the job.
- By Robert Wegner
- Jun 01, 2019
At the start of every new year, I get a sampling of what new technologies are going to be introduced. Most of the time, I’m in way over my head. Sometimes I understand and relate to the solution, the technology and what it all means.

When this upgrade project began in early 2017, there was a mix of standard-resolution legacy video cameras scattered throughout the facilities.
- By Courtney Dillon Pedersen
- Jun 01, 2019

According to Aite Group, a research and advisory firm, losses incurred by account takeovers at contact centers are expected to reach $775 million in 2020, nearly double the amount from just five years ago.
- By Dr. Kornel Laskowski
- Jun 01, 2019

An SDSC is a crime-fighting nerve center that facilitates decision making through increased intelligence and better understanding. Built using dedicated hardware and software solutions, they are housed in local police departments of big and small cities.
- By Giovanni Gaccione
- Jun 01, 2019

Most access control systems are focused on improving security and protecting the business, ensuring that only the right people have the right access to the right areas. It keeps the bad guys out and the good guys in.
- By John Carter
- Jun 01, 2019
Today, artificial intelligence and machine learning are backing a wide range of technologies and applications, powering diverse solutions to a broad set of challenges.
- By Tom Edlund
- Jun 01, 2019

In 2017, the state of California passed Senate Bill 1299, ushering into law a set of regulations requiring California healthcare providers to take specific steps to prevent workplace violence and ensure a safe environment for both patients and caregivers.
- By Paul Baratta
- Jun 01, 2019

It is a story as old as time. Burglars and thieves break into a business, cause major damage to the property, and get away with valuables that can be costly to replace— not to mention potentially company proprietary information.
- By Kaleigh Burton
- Jun 01, 2019

K9s will be used at the Detroit airport to add an additional layer of security in the airport's busiest season.
- By Sydny Shepard
- May 31, 2019

Spain will deploy an unprecedented amount of security for Saturday's "high risk" Champions League final.
- By Sydny Shepard
- May 31, 2019

A transit system near Tampa, Fla. is boosting security measures after a bus driver was stabbed to death by a passenger.
- By Sydny Shepard
- May 30, 2019

After several deadly attacks on houses of worship, legislators are stepping up to find funding to install necessary security solutions.
- By Sydny Shepard
- May 30, 2019
- By Ralph C. Jensen
- May 29, 2019

Dangerously large crowds at Memphis' famous Beale Street led to road closures and arrests over the weekend.
- By Sydny Shepard
- May 29, 2019

One person was shot in the leg Monday morning in what authorities described as a random shooting on the campus of the Arkansas Children’s Hospital.
- By Jessica Davis
- May 29, 2019

First American Financial Corporation was made aware of a flaw that exposed their client's mortgage documents.
- By Sydny Shepard
- May 29, 2019