
Privacy. It’s gone beyond buzzword into a class of its own: basically, privacy of the individual is of the ultimate importance, and all else must fall away in our efforts to preserve it.
- By Arie Melamed
- Apr 01, 2018

It is one of the largest cyberattacks against a major U.S. city.
- By Sydny Shepard
- Mar 30, 2018

San Antonio Police Chief William McManus said his department has partnered with 12 other agencies to collect intelligence and keep the events and attendees safe.
- By Jessica Davis
- Mar 29, 2018

Rome is on high alert following terror warnings that have, so far, turned out to be false.
- By Sydny Shepard
- Mar 28, 2018

The Fire Service was effectively "outside the loop."

Users are downloading their Facebook data to see just how much Facebook is recording.
- By Sydny Shepard
- Mar 27, 2018

Market Research Future found that Industrial Access Control is expected to reach $1.03 billion by 2023.
- By Sydny Shepard
- Mar 27, 2018

The cyber theft campaign was targeting American universities, companies and government entities.
- By Sydny Shepard
- Mar 26, 2018

The video promotes the organization's anonymous reporting system.
- By Sydny Shepard
- Mar 26, 2018

High-ranking security executives at Google, Facebook and Twitter—three of the Internet’s most important technology companies—have announced this week plans to leave their respective positions.
- By Jessica Davis
- Mar 23, 2018

Highway Patrol troopers will join the security team at Majory Stoneman Douglas High School.
- By Sydny Shepard
- Mar 22, 2018

The teenager ultimately decided to share his findings because he was afraid it would not be explained correctly to customers.
- By Sydny Shepard
- Mar 22, 2018
Alan has more than 10 years of commercial security experience.

The suspect in the Austin bombings detonated a bomb in his car as officers closed in.
- By Sydny Shepard
- Mar 21, 2018
UT Austin, Austin Country Club and the neighborhoods in the area are boosting security following the serial bombings.
- By Sydny Shepard
- Mar 21, 2018
Brent awarded for leading collaborative efforts and leading SIA International Relations Committee.
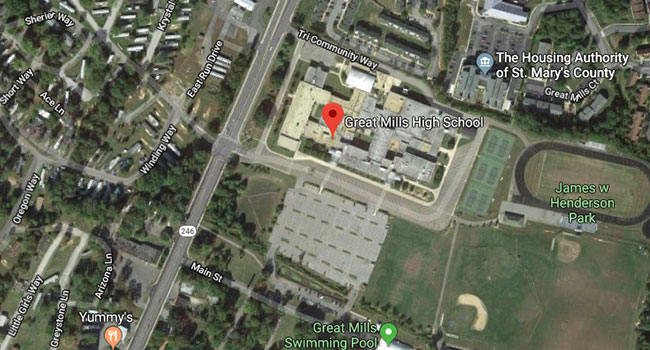
Police in southern Maryland are responding to a call at Great Mills High School were several people have been injured in a shooting.
- By Sydny Shepard
- Mar 20, 2018

According to cybersecurity firm Kromtech, who found it stored in a publicly accessible Amazon S3 bucket.
- By Sydny Shepard
- Mar 20, 2018

Package bombs left on porches in Texas have killed two people and wounded two more.
- By Sydny Shepard
- Mar 19, 2018

Connected devices at home can record the voices, movements, weight and eating habits of those who live there. They are, in effect, very sophisticated sensors installed in the home environment. As such, they can be utilized by all sorts of people with various motivations and intentions of harming us.
- By Yotam Gutman
- Mar 19, 2018

A gunshot-detection system hailed by the Pittsburgh police is poised to cover nearly a third of the city this year.
- By Sydny Shepard
- Mar 19, 2018

Google released its fourth annual review for Android security. Here are the highlights.
- By Sydny Shepard
- Mar 16, 2018

A teacher accidentally discharged a firearm while teaching a public safety class at a Northern California school on Tuesday, according to police.
- By Jessica Davis
- Mar 15, 2018

According to an electronic filing, an unidentified American power company has reached a settlement to pay a $2.7 million penalty over significant security flaws that could have allowed hackers to gain remote access to their systems.
- By Jessica Davis
- Mar 15, 2018

President Donald Trump announced via Twitter that Gina Haspel would be taking the place of Mike Pompeo.
- By Sydny Shepard
- Mar 14, 2018
Technology marches ever forward, lockstep with ‘Moore’s Law.’ However, the influx of technological change affects different industries in different ways.
- By Andy Newbom
- Mar 14, 2018
ISC West attendees are invited to visit Open Options at booth #3103 to learn about the latest features in the DNA Fusion platform, including FlexAPI, Open Options’ application programming interface, OpenDX database exchange software, and DNA Fusion’s Mobile and Web applications.
New Expansion Satisfies Growing Client Needs Across South Central Texas