Complete and fully-functional Silent Knight Fire Alarm and Emergency Communication System serves critical training role in Delaware Tech Fire Engineering Lab.
Analyzes movement in a scene to provide a graphical representation of the areas where the most activity occurred.
Bosch MIC IP 7000 HD family goes IP, captures relevant details in the harshest environments 24/.
Breakthrough encryption and tokenization technologies deliver a new level of safety in today’s risk-prone, online transactional world.

Airport responded that the stowaway posed no security threat because she passed TSA screening.
- By Ginger Hill
- Aug 07, 2014

The company says it has all the markings of a state-sponsored attack.
- By Matt Holden
- Aug 07, 2014

4 ways to battle this social media giant to beat them at their own game.
- By Ginger Hill
- Aug 06, 2014

Russian hackers stole 1.2 billion passwords resulting in the largest collection of stolen internet information.
- By Matt Holden
- Aug 06, 2014

Hospitals operate 24/7. As a result, countless numbers of people enter and exit their facilities. In order to provide a safe environment for their patients and employees, they need to know who these people are and why they are there.
- By Greg Goyne
- Aug 06, 2014
SaaS solution makes SAFE accessible to SMB users and resellers.
Allows healthcare organizations to easily migrate from mechanical locks to electronic access control.
This fast deploying, PSIM value solution helps customers to easily integrate and monitor their entire security environment.
LENSEC representatives will show new features of Perspective Video Management Software.

The internet company found illegal images in his Gmail account.
- By Matt Holden
- Aug 05, 2014

Simplify the process of accessing multiple resources for productivity and collaboration to a "sign and done" experience.
- By Jason Dover
- Aug 05, 2014

In wake of recent bombings, activist group feels need to hack.
- By Ginger Hill
- Aug 05, 2014
The New Video Insight V6 is a Video Management Software (VMS) that provides immediate access to live and recorded video from any server.

A security breach in June might have led to customer data theft.
- By Matt Holden
- Aug 04, 2014
Rigorous, award-winning security officer training program pays off this summer.
Patent #8,736,443 further expands portfolio of AtHoc intellectual property.
Aiphone Corporation's IS-IP Series Networked Video Security Communication System integrates with Lenel’s OnGuard access control security system.
XTec Incorporated awarded long-term work to continue the implementation of the HSPD-12 Program.

Place a round, nickel-sized sticker on your skin where it’s easily accessible and tap your smartphone on the sticker to unlock it.
- By Ginger Hill
- Aug 04, 2014
Jane and Jake work for the same company. This week they’re on one of those dreaded road trips—three cities in four days—and are, as we all are, completely dependent on their tools of choice while on the move.
- By Scott Goldman, Robert Foster
- Aug 01, 2014

Dealing with an obsolete, legacy fire alarm system and a separate, standalone ECS, the building owner’s property management company, Childress Klein Properties, Inc., turned to local Gamewell-FCI distributor Critical Systems LLC, to help them find a new, comprehensive solution.
- By Brian Carlson
- Aug 01, 2014

Choice, cost savings, speed of deployment and convenience. This is what the use of existing legacy cable can afford the end-user as they migrate existing, analog-based surveillance, access control or intercom systems to IP.
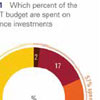
Compliance with increasingly stringent regulations for organizations providing outsourced IT services, particularly in regards to data protection, is becoming more difficult.
- By Gábor Marosvári
- Aug 01, 2014

While the adoption of biometrics has never been more widespread, highly-successful security- and privacy-enhancing applications have been deployed worldwide across all industries; yet, the general public narrative remains focused more on the risks rather than the benefits.
- By Phil Scarfo
- Aug 01, 2014

Distributed Denial of Service (DDoS) attacks are some of the oldest Internet threats and continue to be the top risk to networks around the world.
- By Mark Byers
- Aug 01, 2014

IT professionals are becoming increasingly involved in video surveillance initiatives across all industries. It’s time to build strong relationships with the IT side of the house and include them in discussions about any new system that will piggyback on their backbone.
- By John Bartolac
- Aug 01, 2014