
Place a round, nickel-sized sticker on your skin where it’s easily accessible and tap your smartphone on the sticker to unlock it.
- By Ginger Hill
- Aug 04, 2014
Jane and Jake work for the same company. This week they’re on one of those dreaded road trips—three cities in four days—and are, as we all are, completely dependent on their tools of choice while on the move.
- By Scott Goldman, Robert Foster
- Aug 01, 2014

Dealing with an obsolete, legacy fire alarm system and a separate, standalone ECS, the building owner’s property management company, Childress Klein Properties, Inc., turned to local Gamewell-FCI distributor Critical Systems LLC, to help them find a new, comprehensive solution.
- By Brian Carlson
- Aug 01, 2014

Choice, cost savings, speed of deployment and convenience. This is what the use of existing legacy cable can afford the end-user as they migrate existing, analog-based surveillance, access control or intercom systems to IP.
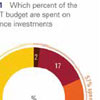
Compliance with increasingly stringent regulations for organizations providing outsourced IT services, particularly in regards to data protection, is becoming more difficult.
- By Gábor Marosvári
- Aug 01, 2014

While the adoption of biometrics has never been more widespread, highly-successful security- and privacy-enhancing applications have been deployed worldwide across all industries; yet, the general public narrative remains focused more on the risks rather than the benefits.
- By Phil Scarfo
- Aug 01, 2014

Distributed Denial of Service (DDoS) attacks are some of the oldest Internet threats and continue to be the top risk to networks around the world.
- By Mark Byers
- Aug 01, 2014

IT professionals are becoming increasingly involved in video surveillance initiatives across all industries. It’s time to build strong relationships with the IT side of the house and include them in discussions about any new system that will piggyback on their backbone.
- By John Bartolac
- Aug 01, 2014

The days of security systems guarding primarily against theft, vandalism and violence are long gone; instead, camera systems are mostly to protect companies against liabilities such as accidents and negligence.
- By Gary Bibeau
- Aug 01, 2014

While businesses will spend thousands of dollars on cameras and recording systems, alarms, intrusion detection, emergency communication and theft prevention, many overlook the need for systems’ power protection.
- By Samantha Wade
- Aug 01, 2014
As the only 24/7 neighborhood in Chicago, River North and Friedman Properties have a shared vision for the area to ensure that success will continue to present itself: aligning the right tenants with the right buildings, demanding the best in security and investing purposefully.
- By Mary Wilbur
- Aug 01, 2014

When officials at the United Illuminating Co., a regional energy distribution company in New Haven, Conn., planned the recent completion of their 56-acre corporate headquarters, their “must-have” list included a campus-wide Emergency Communications System (ECS).
- By David George
- Aug 01, 2014
Some of the most discouraging statistics in the security industry are the record numbers reported in shoplifting from dishonest employees. Recent numbers reported by Jack L. Hayes International shows that those numbers have increased yet again.
- By Ralph C. Jensen
- Aug 01, 2014

From pedestrian-filled farmers markets and universities to new and used car lots, a wide variety of agencies find peace of mind through the use of barriers, bollards, barricades and crash gates for vehicle-based physical access control at the perimeter.

Security clearance is given to thousands of people who owe the IRS money.
- By Matt Holden
- Jul 31, 2014

Safe School Week message: Avenues available to fund door hardware upgrades to better protect teachers and students.
North Carolina security dealer provides hosted services and video verification to homeowners and small businesses.
Funds allocated to freight railroad carriers to strengthen ability to protect against threats and to maintain security of critical surface rail infrastructure.
Loss prevention solution for hospitality users of Squirrel POS Software.

Reverse engineered firmware revealed an embedded controller chip that could be the beginning of wreaking havoc on computer systems.
- By Ginger Hill
- Jul 31, 2014
The IT world is beginning to take notice of cloud surveillance solutions. Case in point, industry newcomer Eagle Eye Networks announced today that Dell computer founder Michael Dell has made a multi-million dollar investment in the company.
- By Brent Dirks
- Jul 31, 2014

Adding to their Nova Series line-up, BCDVideo has begun shipments of the BCD350V8 Video Recording Platform, available in either tower or 5U rack-mount formats.

A look at public space surveillance on either side of the Atlantic highlights how it came of age.
- By David Aindow
- Jul 28, 2014

Here is a list to help develop an all-star team of employees that will protect your information.
- By Matt Holden
- Jul 28, 2014

After millions of dollars spent on perimeter security, no alarm sounded and two men were found.
- By Ginger Hill
- Jul 28, 2014
Because it is a public facility that houses a significant and valuable marine life population, Mystic Aquarium was in need of more sophisticated control of access than traditional methods.

Questions still remain about the implementation and effectiveness of this rule.
- By Matt Holden
- Jul 25, 2014
Company secures U.S. Federal Government facilities in Missouri and Massachusetts.
FST Biometrics' In Motion Identification (IMID) software interfaces with the Lenel OnGuard access control security system.

Typewriter sales in German economy boom as tool to thwart cyber spying.
- By Ginger Hill
- Jul 25, 2014