
In 2022, the tech industry experienced a 649% increase in layoffs. Even before the close of the first quarter of 2023, more than 100,000 employees at US technology companies have been let go. If layoffs persist, particularly in the tech sector, organizations could be at an increased risk of theft of intellectual property (IP).
- By Chuck Randolph
- May 04, 2023

Secretary of Homeland Security Alejandro N. Mayorkas recently announced two new initiatives to combat evolving threats during his first address on the State of the Homeland Security.

Black Kite, provider third-party cyber risk intelligence, recently released its highly anticipated report, “Ransomware Threat Landscape 2023: Ransomware Resurgence”.
UK-based cybersecurity firm Quorum Cyber has announced its intention to focus on the North American market after achieving impressive year-over-year growth.
In advance of RSAC 2023, Sotero has announced the availability of Sotero Ransomware Protection, giving organizations the ability to proactively protect unstructured data from attack by using behavior-based detection.

In new data published today, Darktrace reveals that email security solutions, including native, cloud, and ‘static AI’ tools, take an average of thirteen days from an attack being launched on a victim to that attack being detected, leaving defenders vulnerable for almost two weeks if they rely solely on these tools.

Machine and deep learning algorithms are everywhere in our lives. Masquerading as AI, they are only in their infancy. Have a conversation with a ChatGPT chatbot, and it becomes clear just how far we have come in a short time and how far we have to go.
- By Shawn Kermani
- Mar 27, 2023
In recent years, there has been a significant increase in companies introducing AI technologies for the security surveillance industry. All are promising the ability to deliver some new capability or a better “mousetrap.”
- By Nick Israel
- Mar 22, 2023
We all continue to see common themes across the headlines: Economic downturn, cross-industry job cuts and global geopolitical uncertainty. For businesses around the world, the turbulent situation can create unintended gaps in critical systems or processes that are core to operations.
- By Luke Tenery, Nathan Fisher
- Mar 20, 2023
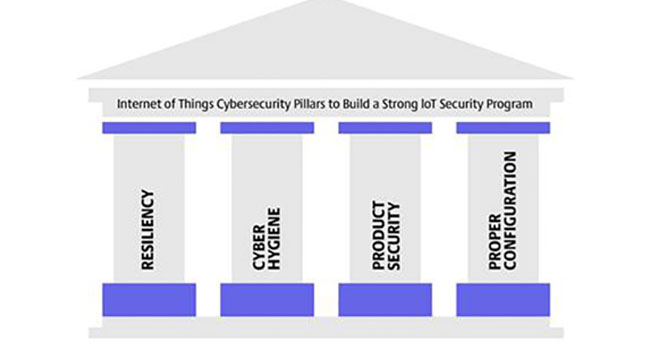
For our second pillar about the Industrial Internet of Things (IIoT) Pillars of Security, we are going to discuss what cyber hygiene looks like for IoT devices.
- By Will Knehr
- Mar 17, 2023
Optiv, the cyber advisory and solutions leader, today announced it has acquired Maryland-based ClearShark LLC and ClearShark Services Inc. (collectively ClearShark), a premier advisor and top value-added reseller of cybersecurity and modernization technology to the federal government.

The world has seen a significant increase in cyber-attacks aimed at critical infrastructure and security products in the last few years, with Industrial Internet of Things (IIoT) devices such as security cameras, becoming prime targets for hackers.
- By Will Knehr
- Mar 10, 2023

The U.S. Environmental Protection Agency (EPA) recently released a memorandum stressing the need for states to assess cybersecurity risk at drinking water systems to protect our public drinking water.

Concentric AI, a vendor of intelligent AI-based solutions for autonomous data security posture management (DSPM), recently announced the availability of its 2022 Data Risk Report, which highlights a continued rise in oversharing of business-critical and sensitive documents. The report revealed the number of overshared files rose 60 percent in 2022 compared to 2021, highlighting the significant impact of hybrid remote work, cloud migration and information sprawl across on-premises and cloud data, as well as email and messaging environments, on data security

The National Security Agency (NSA) released a list of cybersecurity best practices. The information sheet was designed to help teleworkers protect their home networks from malicious cyber actors.
Darktrace today announces the general availability of Darktrace NewsroomTM, an AI-driven system that continuously monitors open-source intelligence sources for new critical vulnerabilities and assesses each organization’s exposure through its in-depth knowledge of their unique external attack surface.

Radware, a provider of cyber security and application delivery solutions, released its 2022 Global Threat Analysis Report. The full-year report leverages intelligence provided by network and application attack activity sourced from Radware’s Cloud and Managed Services, Global Deception Network and threat research team.

In less than four months after its debut, ChatGPT continues to garner attention from users all around the world who have made use of the AI system that answers questions, creates computer code, and much more.
- By Brent Dirks
- Feb 08, 2023

The effects of the pandemic have rippled across the business world like a meteor hitting a pond, creating a new plethora of challenges that incorporated into MBA curriculum for years to come.
- By Bart Vansevenant
- Feb 07, 2023
CTM360, the first Arab world cybersecurity technology operating at a global scale, has captured the Frost & Sullivan 2022 Global Digital Risk Protection Enabling Technology Leadership Award for excellence in commercialization success, application diversity, commitment to creativity and customer service experience.