Scam sinks to new lows by targeting parents with fake “child predator in your area” emails.

One tech expert says biometrics are good, but there are still problems to consider.
- By Matt Holden
- Jan 29, 2015
National Data Privacy Day marked by new technology from TextPower, SnapID that verifies your identity while simplifying website logins and replaces usernames and passwords.
Executives are being targeted with phishing and ransomware to gain network access.

One commercial flight was diverted while two were also evacuated
- By Matt Holden
- Jan 27, 2015

A case of domain hijacking determined by CyberSecurity Malaysia.
- By Ginger Hill
- Jan 26, 2015
First system able to process 2.5 billion transactions per day built for mobile economy; capable of real-time encryption for safest mobile transactions, capable of real-time analytics on transactions 17X faster than competition at a fraction of the cost.
Sera-Brynn discusses cyber security with Vice Pres. Biden and Secretary of Energy Moniz.

Maybe people are becoming number to hearing about "strong, unique passwords."
- By Ginger Hill
- Jan 21, 2015

His emphasis was on protecting families, especially children.
- By Matt Holden
- Jan 21, 2015

The late night host was able to get passwords from strangers off the street in a skit on his show.
- By Matt Holden
- Jan 20, 2015

The Prime Minister is lobbying President Obama this week.
- By Matt Holden
- Jan 16, 2015

Ways in which Obama proposes America fights against cyber threats with commentary from Yubico CEO.
- By Ginger Hill
- Jan 14, 2015

Officials have launched an investigation into the attack
- By Matt Holden
- Jan 14, 2015
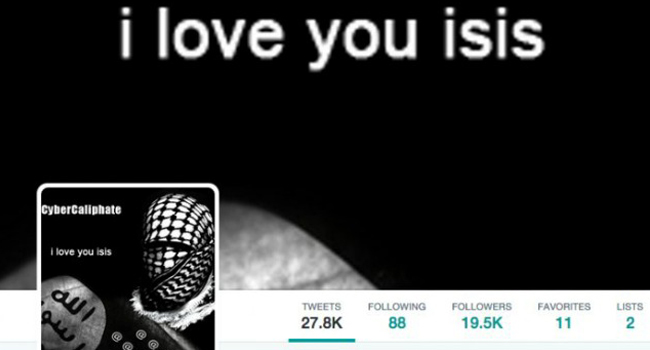
Revealing Tweets from known terrorist group should not be taken lightly.
- By Ginger Hill
- Jan 12, 2015

From his hotel room in Moscow, Edward Snowden has a thing or two to say about digital attacks. (Video included).
- By Ginger Hill
- Jan 09, 2015
Credential provides additional validation of TSC Advantage’s holistic approach to cyber risk assessment.

North Korea’s internet was down for several hours before being restored Tuesday.
- By Matt Holden
- Dec 23, 2014

The BlackBerry Enterprise Server (BES 12) will be integrated into the phone.
- By Matt Holden
- Dec 22, 2014

"The Interview" will not be seen in theaters or on pay-per-view or on any other platform.
- By Ginger Hill
- Dec 18, 2014