EyeLock LLC has announced today that it has secured a global partnership with CMITech Company Ltd. of South Korea.
Mission 500, a charitable non-profit organization engaging security professionals to assist families in crisis across the United States, is proud to announce the launch of its 2020 foundational fundraising campaign – the M500 Club.

Gunshot detection with video analytics, gunshot detection in an indoor environment, and gunshot detection analysis during fire alarms are now exclusive patents held by SDS

In this pandemic of coronavirus, all organizations have shifted from office work to remote work. By saying that, you must have heard about VPNs, and how they improve security and privacy.
- By Susan Alexandra
- Jun 02, 2020
As Mission 500 brings their Feeding America campaign to a close they would like to recognize the countless individuals that stepped up to the “plate” to help feed families across America.

Georgia school officials have released to guidance about how to open campuses for school in the fall by offering a 10-page document “Georgia’s Path to Recovery for K-12 Schools.” The manual was prepared by state education and public health department officials and covers the 2020-21 school year.
- By Ralph C. Jensen
- Jun 01, 2020

While the global pandemic continues to disrupt business, cybersecurity threats increase as companies and workers become even more dependent on digital workflows and tools. Some hackers are leveraging the pandemic as an additional means to spread malware and ransomware. With empty buildings and the rush to enable remote access, it’s never been more important to protect security cameras and accompanying infrastructure from threats.
- By Aaron Saks
- Jun 01, 2020

CEDIA Expo 202 has been canceled and will be held in September 2021 in Indianapolis.
- By Ralph C. Jensen
- Jun 01, 2020

TSA officers detected a loaded handgun at one of the checkpoints at Washington Dulles Airport on Sunday. Airline passengers still attempt to bring handguns on board. So far this year, TSA has found four weapons at security check points.
Paxton Access is introducing a new online access control training program this week. Easily accessible via their website, it offers installers more options and opportunities to enhance their skills anytime, anywhere.

With the global digital transformation, many of the interactions that enterprises have with their customers are shifting online.
- By Ralph C. Jensen
- May 28, 2020
Maxxess Systems is pleased to announce their partnership with Seek Thermal, an advanced imaging technology company, to deliver a complete temperature screening solution to help manage health risks.

Based on a recommendation by DHS and its intergovernmental partners, such as the Centers for Disease Control, President Trump has signed a proclamation on May 24 and amended on May 25 suspending the entry into the United States of any foreign nationals who were present in Brazil during the 14-day period preceding their entry or attempted entry into the United States.
Camden is introducing a new 36-inch tall stainless-steel model to their extensive line of aluminum, dark bronze and blue CM-75 Series ‘Column push plate switches.
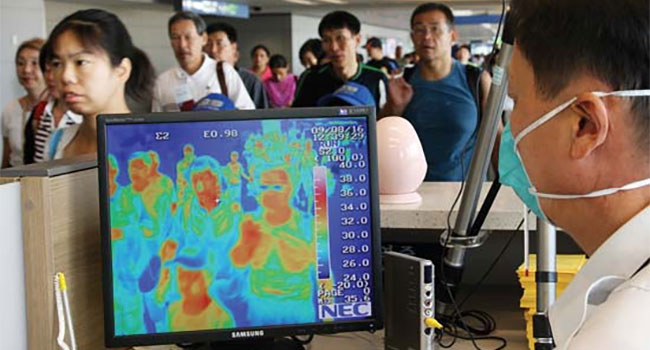
After TSA rolled out a series of new measures May 21, meant to encourage social distancing and stop the spread of COVID-19, the agency also is thinking about checking temperatures and thermal imaging to help screen for the virus.
- By Ralph C. Jensen
- May 27, 2020

13,720 cloud-managed cameras deployed in a cyber-secure city-wide surveillance program using 4G connectivity
Immix has announced today that Chris Brown will take over as CEO and will oversee the global business from end-to-end.

Experiencing an exponential rise of COVID-19 related security cases during the pandemic, International SOS sheds light on three emerging security challenges. These are alongside underlying security issues that the pandemic environment has and will continue to exacerbate.
- By Ralph C. Jensen
- May 26, 2020