
Georgia school officials have released to guidance about how to open campuses for school in the fall by offering a 10-page document “Georgia’s Path to Recovery for K-12 Schools.” The manual was prepared by state education and public health department officials and covers the 2020-21 school year.
- By Ralph C. Jensen
- Jun 01, 2020

While the global pandemic continues to disrupt business, cybersecurity threats increase as companies and workers become even more dependent on digital workflows and tools. Some hackers are leveraging the pandemic as an additional means to spread malware and ransomware. With empty buildings and the rush to enable remote access, it’s never been more important to protect security cameras and accompanying infrastructure from threats.
- By Aaron Saks
- Jun 01, 2020

CEDIA Expo 202 has been canceled and will be held in September 2021 in Indianapolis.
- By Ralph C. Jensen
- Jun 01, 2020

TSA officers detected a loaded handgun at one of the checkpoints at Washington Dulles Airport on Sunday. Airline passengers still attempt to bring handguns on board. So far this year, TSA has found four weapons at security check points.
Paxton Access is introducing a new online access control training program this week. Easily accessible via their website, it offers installers more options and opportunities to enhance their skills anytime, anywhere.

With the global digital transformation, many of the interactions that enterprises have with their customers are shifting online.
- By Ralph C. Jensen
- May 28, 2020
Maxxess Systems is pleased to announce their partnership with Seek Thermal, an advanced imaging technology company, to deliver a complete temperature screening solution to help manage health risks.

Based on a recommendation by DHS and its intergovernmental partners, such as the Centers for Disease Control, President Trump has signed a proclamation on May 24 and amended on May 25 suspending the entry into the United States of any foreign nationals who were present in Brazil during the 14-day period preceding their entry or attempted entry into the United States.
Camden is introducing a new 36-inch tall stainless-steel model to their extensive line of aluminum, dark bronze and blue CM-75 Series ‘Column push plate switches.
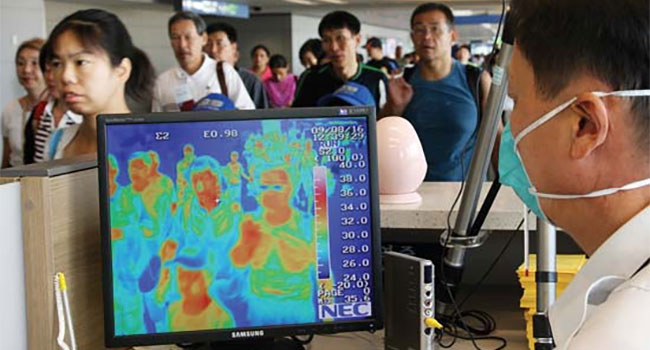
After TSA rolled out a series of new measures May 21, meant to encourage social distancing and stop the spread of COVID-19, the agency also is thinking about checking temperatures and thermal imaging to help screen for the virus.
- By Ralph C. Jensen
- May 27, 2020

13,720 cloud-managed cameras deployed in a cyber-secure city-wide surveillance program using 4G connectivity
Immix has announced today that Chris Brown will take over as CEO and will oversee the global business from end-to-end.

Experiencing an exponential rise of COVID-19 related security cases during the pandemic, International SOS sheds light on three emerging security challenges. These are alongside underlying security issues that the pandemic environment has and will continue to exacerbate.
- By Ralph C. Jensen
- May 26, 2020

Rep. Buddy Carter (R-Ga.) recently introduced H.R. 6929, the Advancing Facial Recognition Act, which requires the Federal Trade Commission, the U.S. Department of Commerce and other appropriate agencies
- By Joe Hollered
- May 26, 2020

An unidentified shooter has injured on security guard at Naval Air Station Corpus Christi, TX, today. It has been determined that the shooting is terrorism related, according to the FBI.
- By Ralph C. Jensen
- May 21, 2020

The legislation addresses the purchase of airport equipment, particularly passenger boarding bridges, from countries that are known for IP theft or national security threats.
- By Haley Samsel
- May 21, 2020
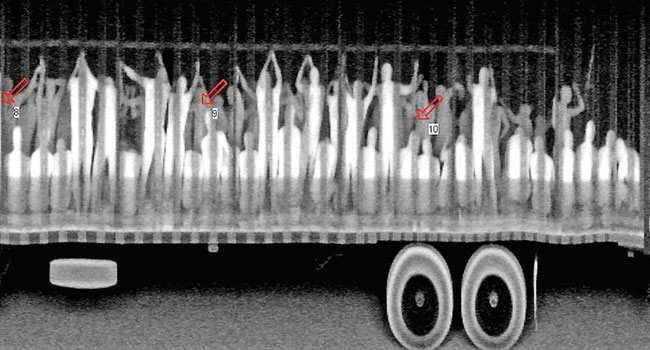
Human smugglers continue to plague law enforcement and society at large, despite the COVID-19 pandemic and without regards to several Customs and Border Protection policies and travel restrictions aimed at preventing the spread of the disease. Smugglers continue to place migrants in harm’s way.
- By Ralph C. Jensen
- May 20, 2020