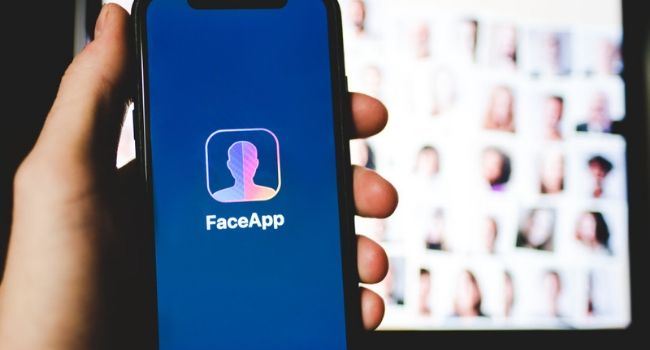
The app, which is based out of Russia, was popular for its ability to make users look older. But critics say there’s a catch.
- By Haley Samsel
- Jul 19, 2019
Company to integrate CylancePROTECT into Streamvault appliances

Lawmakers are concerned about the use of out-of-date software on voting systems across the United States, but no new legislation has been passed in both chambers.
- By Haley Samsel
- Jul 18, 2019

A state audit found that the personal information of over 1 million students and more than 200,000 teachers was at risk of identity theft.
- By Haley Samsel
- Jul 18, 2019

Both measures, which aim to improve the Small Business Administration and resources for business owners, were adopted with bipartisan support.
- By Haley Samsel
- Jul 17, 2019

The company records a continuous growth in expanding markets.

The 12-year-old boy was traveling unaccompanied and did not have travel documents. But he was still able to board a flight to Los Angeles.
- By Haley Samsel
- Jul 17, 2019

While the penalty will have little effect on Facebook’s bottom line, the massive fine could be indicative of the commission’s willingness to punish companies for data security issues.
- By Haley Samsel
- Jul 16, 2019

IN FORCE 911 allows staff to quickly launch an emergency alert and facilitates quick communication between victims and police.
- By Haley Samsel
- Jul 16, 2019

The $10 billion JEDI project has been rife with controversy, but the Pentagon still hopes to seal the deal with one of the companies next month.
- By Haley Samsel
- Jul 15, 2019

A California-based company has been given the OK to offer its services to campaigns for a discounted rate — as long as that rate is the same for other clients.
- By Haley Samsel
- Jul 15, 2019

The agency said it screened over 11.9 million passengers and crew as well as over 8 million checked bags during the holiday travel period.
- By Haley Samsel
- Jul 12, 2019

The legislation would require the Department of Homeland Security to develop educational resources for business owners and train counselors on higher-level cybersecurity information.
- By Haley Samsel
- Jul 12, 2019

A recent public meeting exposed tensions about how a city-wide video surveillance system is being used to identify crime suspects in Detroit.
- By Haley Samsel
- Jul 11, 2019

Respondents, who answered 22 percent of questions incorrectly, struggled most with assessments about mobile device encryption and protections for personally identifiable information.
- By Haley Samsel
- Jul 11, 2019

The airline, along with Mariott International, is facing harsher penalties for not properly protecting customers’ personal data prior to cyberattacks.
- By Haley Samsel
- Jul 10, 2019

The company, Zoom, is now taking action to update its software after a security researcher discovered several serious security vulnerabilities in the popular video chat app.
- By Haley Samsel
- Jul 10, 2019

If the Securing Energy Infrastructure Act is signed into law, it will create a working group tasked with isolating the energy grid from attacks using “manual procedures.”
- By Haley Samsel
- Jul 09, 2019