
Businesses in the city of Saginaw, Michigan have until March 1, 2019 to install three security cameras at each building and put up parking lot lights.
- By Sydny Shepard
- Feb 20, 2018

The risk associated with progress is always great and must be considered at all times.
- By Greg Robinson
- Feb 19, 2018

The Election Security Act would provide $1 billion for the U.S. Election Assistance Commission to give to states to buy voting machines.
- By Sydny Shepard
- Feb 16, 2018

Video from the school's surveillance system has helped police put together a timeline of events on the day of the shooting.
- By Sydny Shepard
- Feb 16, 2018

The 19-year-old shooter is now in custody.
- By Ralph C. Jensen, Sydny Shepard
- Feb 14, 2018

An NSA spokesman said the incident is under control.
- By Sydny Shepard
- Feb 14, 2018
“When dealers talk to me about their RMR, the first thing I ask is for them to break it down for me. That’s often when things bog down.
- By Scott MacDougal
- Feb 14, 2018

Cybersecurity firms are confirming that a computer malware attack dubbed "Olympic Destroyer" hit Wi-Fi systems at the Winter Games.
- By Sydny Shepard
- Feb 14, 2018
Awards $1000 to University of Maine Student
Empowering Integrators to Maximize Collaboration, Sales and Margins

Washington state’s new cannabis-tracking system was hacked the weekend of Feb. 3, according to the Washington State Liquor and Cannabis Board (WSLCB). Among other information, the hacker stole route information associated with four days of marijuana deliveries.
- By Jessica Davis
- Feb 12, 2018

Relatively new on the market, the iKeyp is a smart safe for everyday use. It is simple to install and easy to connect with via the app on your smartphone.
- By Ralph C. Jensen
- Feb 12, 2018

Beginning in July with the release of Chrome 68, Google Chrome will mark all HTTP sites as “not secure”. The Chrome browser already displays a green lock icon and “Secure” sign in the URL bar for HTTPS-encrypted websites.
- By Jessica Davis
- Feb 12, 2018

You’ll get a real kick out of this security story. It is all about a secure perimeter and access control that is stored in the cloud and a man devoted to those around him.
- By Ralph C. Jensen
- Feb 12, 2018
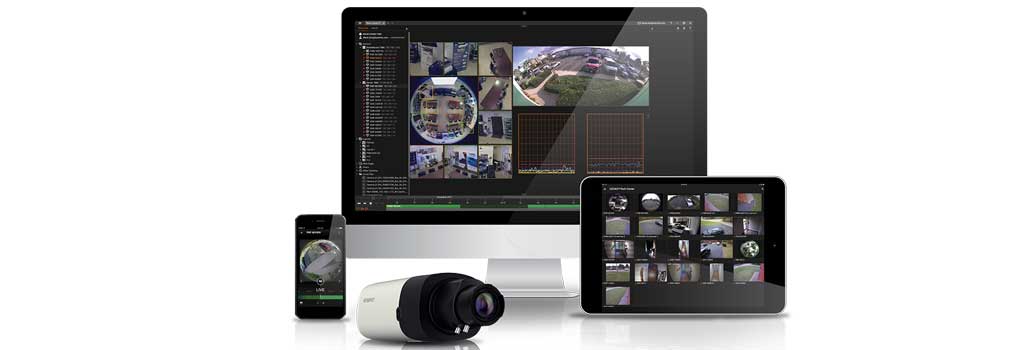
Ideal for customers seeking an easy to use end-to-end video surveillance solution, WAVE is highly customizable and can create tailored network video solutions for any type of project, on any device.

Consumer Report says its testing found that Roku devices and Samsung Smart TVs have security flaws that make them vulnerabilities to hackers.
- By Sydny Shepard
- Feb 09, 2018