August Home strengthens ASSA ABLOY’s residential smart door strategy with complementary smart locks.

The bill comes in the wake of news that Uber handled a breach affecting as many as 57 million consumers by paying the hackers $100,000 in exchange for their silence.
- By Jessica Davis
- Dec 05, 2017

Despite the answers a bit of saliva can provide, some are critical of the at-home test services, questioning the level of security they provide for your most sensitive information.
- By Jessica Davis
- Dec 05, 2017
ESP Company Pact Reflects Smart Power Systems Expansion into SE Region

The year 2017 undoubtedly saw the connected automotive business grow dramatically, and by 2020 over 250 million connected cars are set to hit the roads.
- By Andy Allan
- Dec 04, 2017

Wink has produced a starter kit for consumers looking to add smart functionality to their homes.
- By Sydny Shepard
- Dec 04, 2017

Technology is perpetual motion personified. It is always marching forward, striving to become smarter, faster, more resilient, and more efficient than its predecessor.
- By Fredrik Nilsson
- Dec 01, 2017

The 300,000 person Fremont Festival of the Arts, one of the largest street festivals west of the Mississippi River and toted as California’s premiere art, wine and music festival, is no small undertaking. The threat of an attack is a real possibility.
Should more parishioners carry guns in church? Texas Attorney General Ken Paxton says yes, because as he sees it: “This is going to happen again.”
- By Ralph C. Jensen
- Dec 01, 2017
Some of the industry trends which have affected technology and deployment design include a dramatic cost reduction in entry level NVRs and cameras.
- By Brian Carle
- Dec 01, 2017

Only a few years ago, the inevitable shift to all things Cloud was met with guarded optimism. But today, the shift is really happening.
- By Christian Morin
- Dec 01, 2017
Because Involta houses an organization’s most critical equipment and disseminates highly sensitive data, their facilities required a layered approach to their security solution—including access control, video surveillance, wireless locks and more—to ensure access is granted only to the appropriate person.
- By Ellie Randall
- Dec 01, 2017

As video manufacturers have been driven to differentiate themselves in the marketplace, high-end surveillance technologies have become accessible to a much broader customer base. One technology of note is thermal imaging.
- By John Distelzweig
- Dec 01, 2017

NYPD increased the security measures for this year’s Christmas tree lighting due to heightened vigilance in the wake of the truck attack in Tribeca in October.
- By Jessica Davis
- Nov 30, 2017

Police and a sheriff’s SWAT team raided the room and the suspect died shortly after being taken into custody.
- By Jessica Davis
- Nov 30, 2017
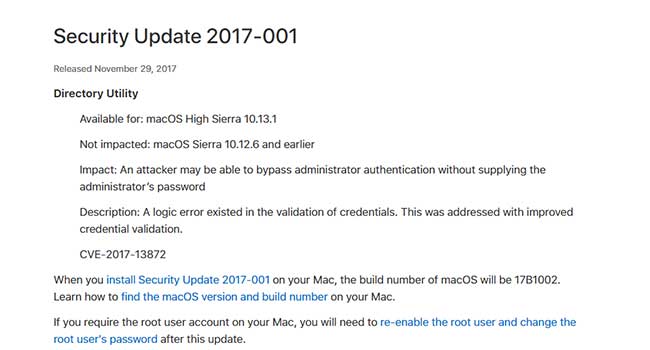
Apple has patched a macOS High Sierra flaw that would allow intruders to gain full administrator access on your system.
- By Jessica Davis
- Nov 30, 2017

A California man was arrested Sunday after he allegedly piloted a drone over two NFL stadiums in an attempt to distribute “anti-media” pamphlets to the crowds below.
- By Jessica Davis
- Nov 29, 2017

Being online puts you and your data at risk, but there are ways you can minimize your risk and make a hacker’s job harder.
- By Jessica Davis
- Nov 29, 2017