
Manitowoc sheriffs have now been targeted in more ways than one for their role in Steven Avery’s case.
- By Sydny Shepard
- Feb 04, 2016

The rugby match will be the first one played at the Stade de France since the Paris Attacks.
- By Sydny Shepard
- Feb 03, 2016
Rep Organization to Manage Sales Activity in Eastern Canada
- By Sydny Shepard
- Feb 03, 2016

Researchers find the Motorola Focus 73 security camera to have a pretty big vulnerability.
- By Sydny Shepard
- Feb 03, 2016
Hutt has 25 years of experience in the industry

Bank robbers aren’t the only ones that will demand cash from your accounts.
- By Sydny Shepard
- Feb 02, 2016
Providing Consistent Solutions for Sun Control Since 1966
Each quarter, Camden will select one entry to receive a $500 Visa Gift Card prize. Winners will be featured on the Camden website, Facebook page and social media sites.

Facebook announces they will be banning private gun sales on its site, a move meant to clamp down on unlicensed gun transactions.
- By Sydny Shepard
- Feb 01, 2016
The MasterCard Card Quality Management audit covers HID Global’s contactless and dual interface inlays for banking and payment solutions.
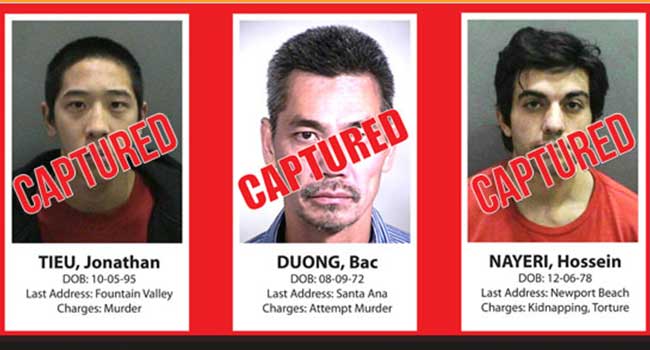
Three California inmates who escaped from a maximum security facility have been recaptured. Now the investigation focuses on how it happened.
- By Sydny Shepard
- Feb 01, 2016

The remote geographic location with each island being separated by miles of ocean posed some challenges for the project, making air, land and sea transportation necessary to complete the job.
- By Kim Rahfaldt
- Feb 01, 2016

The daily increase in the number of cyber attacks launched and the success hackers are having against heavily guarded businesses are a wake-up call for all companies to be more proactive and vigilant in their security efforts.
- By Gregory Grant
- Feb 01, 2016

Successful companies read the tea leaves and saw IoT-connected devices coming. This includes video surveillance, which is now among the fastest growing industries in terms of data generation and adoption of new data storage technologies.
- By Brian Grainger
- Feb 01, 2016

Because of recent news and my frequent visits through the security checkpoint, I have come to lack confidence in TSA employees.
- By Ralph C. Jensen
- Feb 01, 2016

For many years, physical and network security existed as separate disciplines, each managed by an independent operations team on its own side of the house with little or no crossover between the two.

Every summer, the Saratoga Race Course brings thousands of visitors to the City of Saratoga Springs, NY. The revenue generated during the racing season boosts the city’s economy for the rest of the year.
- By Courtney Dillon Pedersen
- Feb 01, 2016
Thirty years ago, maybe more, the dream of the IP camera was about to make its debut. The technology, as I remember it, wasn’t all that well received, but that didn’t mean it was a bad idea. It became an exercise of marketing the future to the here and now.
- By Ralph C. Jensen
- Feb 01, 2016