
A wayward driver. A medical emergency. Maybe someone who wants to inflict harm. These are all examples of a vehicle jumping on a sidewalk and causing injuries to pedestrians and workers. It is impossible to foresee every potential scenario where this might happen but the one solution that can stop the vehicle from doing damage are crash-rated bollards, with an emphasis on “crash rated.”
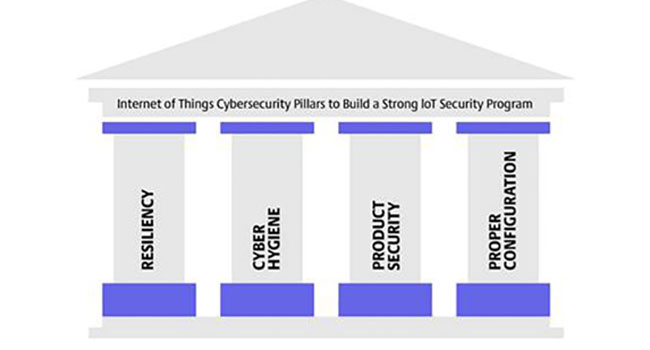
The world has seen a significant increase in cyber-attacks aimed at critical infrastructure and security products in the last few years, with Industrial Internet of Things (IIoT) devices such as security cameras, becoming prime targets for hackers.
- By Will Knehr
- Mar 10, 2023

Necessity may be the mother of invention, but Rently is the mother of inventing self-guided touring for rental properties.
- By Erik Glassen
- Mar 10, 2023

The U.S. Environmental Protection Agency (EPA) recently released a memorandum stressing the need for states to assess cybersecurity risk at drinking water systems to protect our public drinking water.
Paxton has made an exciting update to their US sales team structure to provide a laser focused approach across the United States.

Changes to our digital spaces in recent years have led to an increase in IT risk—especially in the healthcare space. With more digitization comes an increased number of risks. Nearly 85% of healthcare data breaches reported to the HHS Office for Civil Rights (OCR) in 2022 were attributed to hacking and IT incidents, according to data from the HHS. With more determined threat actors wanting to exploit patient data, a proactive approach to seeing, understanding and acting on risk is vital to improving the effectiveness of security.
- By Chasserae Coyne
- Mar 08, 2023
Cozaint Corp. has been selected by WGS Group, Inc., a security guard services company with headquarters in Las Vegas, NV, and servicing California, Texas, Florida, and other states, to deliver the BOBBY physical security kiosk system to their customers.
Allied Universal® today announced the appointment of Tom Rulon as vice president, business development -- Event Services.
The Security Industry Association (SIA) has named Kim Loy and Brendan McFall as the 2023 recipients of the SIA Chair’s Award, an award presented annually and selected by SIA’s Board of Directors chair recognizing SIA members’ diligent efforts in furthering the association’s mission and commitment to its future.

Motorola Solutions released the results of its Healthcare Worker Safety Report after surveying 500 respondents, including doctors, nurses, technicians and administrators between December 2022 and January 2023.

After 20 years on the market, it is safe to say that wireless electronic access control (EAC) has hit the mainstream. In 2022, wireless solutions dominated the major projects involving digital access solutions, and the trend appears to be growing as organizations ramp up plans for 2023. The primary drivers revolve around wireless EAC’s affordability, faster and easier installation, greater scalability, labor efficiency, and compatibility with wired solutions.
- By Lester LaPierre
- Mar 03, 2023

With inflation rising and rumors of a recession haunting boardrooms all over the country, smaller security budgets are expected to be a reality for businesses in 2023. As a result, companies will tighten their belts to adjust to the changing economic landscape.

When assessing whether turnstiles are appropriate for your facility, ask this first question: What are you trying to achieve?
- By Kassi Karr
- Mar 01, 2023
Milestone Systems announces that effective today, Rahul Yadav joins the company from TV 2, the Danish commercial public service broadcaster.

Hanwha Techwin has changed its name to Hanwha Vision, as the company expands its offerings as a global vision solutions provider committed to fully supporting the changing needs of customers and partners.
Genetec Inc. has announced a new collaboration with Axis Communications that will see the introduction of Axis Powered by Genetec, the industry’s first enterprise-level access control offering that combines Genetec access control software with Axis network door controllers in a single easy-to-deploy all-in-one offering.

Concentric AI, a vendor of intelligent AI-based solutions for autonomous data security posture management (DSPM), recently announced the availability of its 2022 Data Risk Report, which highlights a continued rise in oversharing of business-critical and sensitive documents. The report revealed the number of overshared files rose 60 percent in 2022 compared to 2021, highlighting the significant impact of hybrid remote work, cloud migration and information sprawl across on-premises and cloud data, as well as email and messaging environments, on data security
Advanced detection technology helps provide a safe environment at the Iconic Venue