
The esports industry calls for increased security following the death of two esports players at a tournament.
- By Sydny Shepard
- Aug 28, 2018

Last week was not a good week for telecommunications companies.
- By Sydny Shepard
- Aug 28, 2018
Netwatch Group appoints Mike Taylor as VP of US Sales, unifying the US presence and introducing a single sales organization.
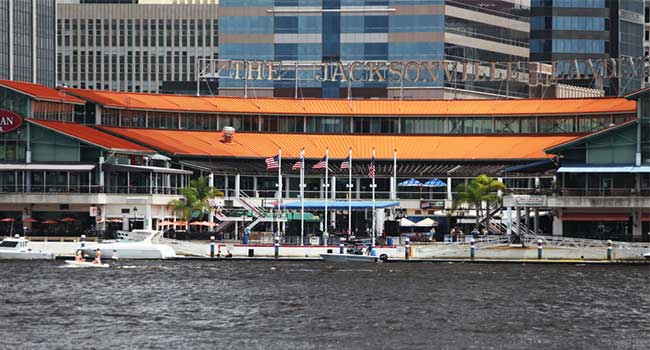
Two people were killed and several others were injured by a gunman at a Madden 19 tournament in Jacksonville, Fla.
- By Sydny Shepard
- Aug 27, 2018

Armed guards and metal detectors are chief among the new measures being taken to ensure the safety of patients.
- By Jordan Lutke
- Aug 24, 2018

Police were able to track down a suspect after receiving security camera footage from a home near the site where Mollie Tibbetts disappeared.
- By Sydny Shepard
- Aug 23, 2018

Even if guests put up a “Do Not Disturb” sign on their door, security will enter the room to perform the search.
- By Jordan Lutke
- Aug 23, 2018

The threats of cyberattacks are increasing, spurring the recent invention and patenting of technologies like freeze logic.
- By Jordan Lutke
- Aug 22, 2018

The city is looking into adding plexiglass dividers between drivers and riders to cut down on assaults.
- By Sydny Shepard
- Aug 21, 2018

TheBestVPN found vulnerabilities in several big name routers.
- By Sydny Shepard
- Aug 21, 2018

Banks are on alert after the FBI warned of a new potential threat.
- By Sydny Shepard
- Aug 20, 2018

Beginning Wednesday, security officers were stationed at all entrances to help guide visitors to the appropriate areas. Security at the facility is also limiting entrance to the hospital to three locations and the Emergency Department.

Security Today has announced the winners of the annual New Product of the Year contest.
- By Sydny Shepard
- Aug 16, 2018

The Los Angeles Metro will be the first public transit system in the United States to purchase millimeter wave scanners to screen riders for suspicious objects such as weapons and explosives, officials announced Tuesday.
- By Jessica Davis
- Aug 16, 2018

Seattle-Tacoma International Airport is reviewing and increasing security measures after a ground-service agent stole a plane and crashed it into a south Puget Sound island on Friday. According to an airport spokesman, the agent was one of about 13,600 people with access to aircraft at the airport.
- By Jessica Davis
- Aug 15, 2018

By following these five tips, you can make your property as secure as possible while you’re away.

When you print, scan, or copy anything at home or in the office, the data on the printed page makes it possible to track both you and your documents.

With the rapid adoption of the Internet of Things (IoT), we are moving towards an entirely interconnected world, from smart organizations to smart cities.

The company quickly resolved the problem in its Xfinity customer software.
- By Sydny Shepard
- Aug 10, 2018

YouTube intends to bulk up security at the company's headquarters after a shooting on campus that injured three people.
- By Sydny Shepard
- Aug 09, 2018

Seattle sporting venues to improve security with biometric platform.
- By Sydny Shepard
- Aug 09, 2018
Joint solution already in use at DICK’S Sporting Goods to provide immediate insight, reduce shrink, improve profitability and achieve rapid ROI

A test last year showed gate checks using the facial recognition was more than twice the pace of the conventional system using x-ray with visual siting by security guards.
- By Sydny Shepard
- Aug 08, 2018

The move comes after several high profile homicides and other violent crimes on the BART system.
- By Sydny Shepard
- Aug 08, 2018
HID Global announced the appointments of two high-profile senior executives to the HID leadership team