
MacSpy is being advertised as the “most sophisticated Mac spyware ever.”
Leading security systems integrator now carries the Zebra ZC10L direct-to-card printer that can produce full, edge-to-edge oversized cards in one printing process.

A Georgia inmate shot and killed two correctional officers and now two prisoners are on the run.

The incident that left 49 dead happened one year ago.

Security will be stepped up at polling stations during the general election in UK in light of the London terror attack.

President Trump says he has chosen Christopher Wray to head the FBI.
We are pleased to welcome the newest members of the Speco team.
They're setting the new industry standard for quality, features and affordability.

Two females were injured after a man entered the beauty college and open fired. He then shot and killed himself.

Orange County Sheriff’s Office confirmed five people were killed in a workplace violence incident in Orlando, Florida.

Police in London say they used unprecedented amount of force to ensure the London attackers were neutralized in less than ten minutes.
Regional Sales Managers for the Midwest, Southwest, Northeast and Florida Join the Vicon Team
Per Mar Security Services is pleased to announce it has acquired Southlake Security in Griffith, Indiana further expanding its security services and customer base in Northwest Indiana.

Ariana Grande and company are playing a benefit concert to raise funds for the victims of the Manchester Arena bombing. Here’s how they’ll keep it safe.

While many security teams at retailers are concerned about the potential for a big data breach, everyday security threats, like social engineering and shoplifting, are heightened in a world of omni-channel retail.
- By John Carter
- Jun 01, 2017

The Beer Cellar, located in Glen Ellyn Park, Ill., recently transitioned to a new storefront that not only provided expanded business opportunity but also required added safety and security measures in a busy and highly functional space.
- By Larry Chay
- Jun 01, 2017

When seconds count in an emergency, such as an active shooter or severe weather, gaps in communication can cost lives. Many schools, businesses and healthcare facilities face the challenge of ensuring comprehensive coverage with their existing emergency mass communication systems.
- By Greg Smith
- Jun 01, 2017

With a pending network overhaul and the fast-approaching emergency exercise, Pangborn Memorial Airport was driven to action.
- By Michael Hardy
- Jun 01, 2017

The National Park Service has an extensive security protocol for its numerous locations nationwide, though they do stress an extensive layered approach.
- By Ralph C. Jensen
- Jun 01, 2017

A family-oriented municipality with a thriving business environment, the city of Cypress is home to 48,000 residents in North Orange County, Calif.
- By Ralph C. Jensen
- Jun 01, 2017
Sometimes you need to be in the right place at the right time. Sometimes, it’s who you know. For Karrie Gabbard, executive director of the East Butler County Family YMCA in Hamilton, Ohio, it was both.
- By Kim Rahfaldt
- Jun 01, 2017
The risk posed by hackers to the Internet of Things (IoT) is a hot topic and there have already been some serious real-world attacks.
- By Christopher Camejo
- Jun 01, 2017
The Center for Puppetry Arts commissioned Atlanta’s Operational Security Systems (OSS) to provide security including access control for both phases of the construction project. The challenge included many key components.
An active shooter on campus has no rhyme or reason. When something stupid like this happens, everyone’s first question is: Why? Followed by: What was the motive?
- By Ralph C. Jensen
- Jun 01, 2017
- By Kathleen Hannon
- Jun 01, 2017
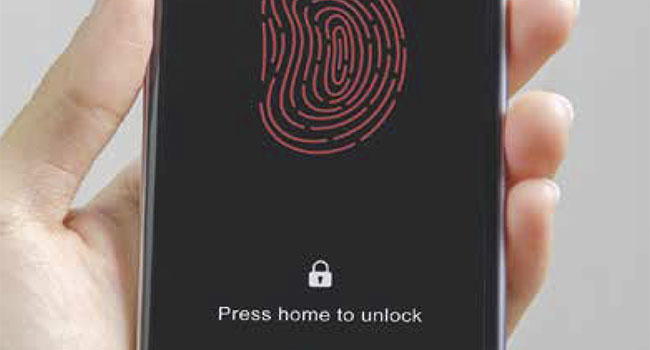
When used effectively, biometrics can contribute to safer cybersecurity practices.
- By Alisdair Faulkner
- Jun 01, 2017

Port Angeles, located on the U.S.-Canada border, is host to a thriving maritime port and a significant customs entry point into the United States.
- By Dwight Dumpert
- Jun 01, 2017

Many industries have successfully implemented video surveillance and management systems in their manufacturing facilities as a way to reduce the risk of theft or vandalism.
- By Brent Dirks
- Jun 01, 2017
Sessions Help Users Navigate Door and Lock Options