
The most recent elections is the most secure in the nation’s history. Or, is it? Government officials say it is the most secure ever.

The 2020 election season is a Big Deal as well it should be. The Vote, as foundational parts of the whole, is complicated in practice with history showing us just how complicated it can be. Protecting the process and making sure the Vote is fair, secure, and timely, is vital to American Democracy.
- By Saryu Nayyar
- Oct 28, 2020

The Trump Administration continues its work to ensure America’s technological and innovative edges are guaranteed by offering the first National Strategy for Critical and Emerging Technology.

The recent release of a massive cache of sensitive Law Enforcement data has been in the news recently. The trove of roughly 270 gigabytes of data posted to the Denial of Secrets website has been referred to as “BlueLeaks.”
- By Nilesh Dherange
- Oct 13, 2020
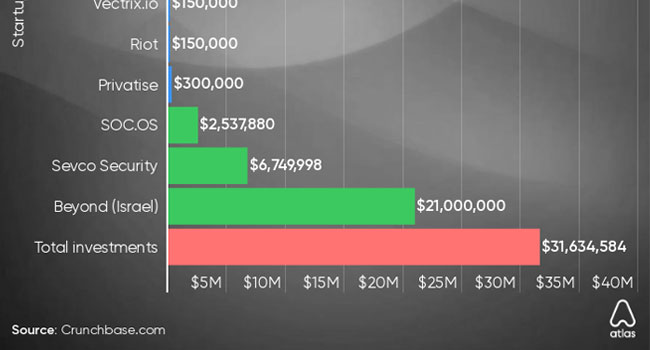
According to data presented by the Atlas VPN team, there are 78 new cybersecurity companies founded in 2020 that cumulatively have raised over $31.6 million in funding year-to-date.
Crowdsourcing effort to uncover security issues is latest addition to company’s broader cybersecurity strategy
Due to the nature of cyber-physical systems (CPSs), incidents can quickly lead to physical harm to people, destruction of property or environmental disasters. Gartner analysts predict that incidents will rapidly increase in the coming years due to a lack of security focus and spending currently aligning to these assets.
With digital transformation comes the move to the cloud. What many businesses don’t realize is that it requires a retooling of their security strategy from the ground up.
- By Eric Kedrosky
- Sep 15, 2020
McAfee today announced its latest consumer security portfolio that includes enhanced products with better user experiences such as a native VPN and new features, including integrated social media and tech scam protection.
According to the Confidential Computing Consortium: “Confidential computing is the protection of data in use using hardware-based Trusted Execution Environments (TEE).
- By Richard Searle
- Sep 14, 2020

The Security Industry Association (SIA) has released its new policy principles guiding the development and deployment of facial recognition technology.
The Trump Administration announced the first comprehensive cybersecurity policy for systems used in outer space and near space Sept. 4.
Many of the cyberattacks on state, local, tribal and territorial governments are not complicated and could be avoided through simple steps such as improved cyber hygiene and two-factor authentication, a new report states.
- By Stephanie Kanowitz
- Sep 08, 2020

Video surveillance is commonplace today, but many organizations don’t even realize that they aren’t fully leveraging the video data that their cameras capture. Traditionally, law enforcement and physical security teams use video cameras to monitor areas in real-time and to review footage to glean evidence for post-incident investigation.
- By Stephanie Weagle
- Sep 03, 2020

USB drives are convenient devices. They are used daily by hundreds of millions of people around the world to store or transport data, much of which would be considered confidential. Chances are there are plenty of USB drives floating around your company or organization right now.
- By Richard Kanadjian
- Sep 03, 2020
Cloud security is an increasing concern as more organizations transition to use public cloud providers in either a hybrid or cloud-native model.
- By Cliff Krahenbill
- Aug 07, 2020

As the Internet of Things (IoT) becomes mainstream, companies are delving into the ramifications of adoption, including its benefits, challenges, and opportunities--not least, the implications to security and cybersecurity.
- By Steven Turney
- Jul 30, 2020

Prior to the COVID-19 pandemic, the rate of cloud adoption was growing steadily. Since March, however, when “shelter-in-place” orders began sweeping the nation, we’ve seen cloud computing usage skyrocket.
- By Joe Vadakkan
- Jul 30, 2020

In the battle for security budget funding, enterprise key management isn’t nearly as sexy as technologies such as threat hunting or blockchain cybersecurity.
- By David Greene
- Jul 21, 2020
Today, data is often encrypted at rest in storage and in transit across the network, but not while in use in memory. Additionally, the ability to protect data and code is limited in conventional computing infrastructure.