
The smart home industry has exploded with new technology devices
- By Abe Schryer
- Jul 28, 2017

While flexibility is empowering the workforce, it is also complicating data security.
- By David Konetski
- Jul 20, 2017

After the summer rush, TSA may change up their security procedures.

It’s time to take the pledge to improve your password habits.

While these unmanned aircrafts are mostly used professionally and recreationally to add depth and intrigue to films and videos, security teams need to be aware of the threats they could pose on those below.
- By Sydny Shepard
- May 01, 2017
Uber knows where to find you even if you do delete the app.
Three years ago, Shrader Engineering had the privilege of designing one of the most unique security concepts in the region for the city of Sugar Land, Texas, Police Department. The security system forms a “virtual gateway” throughout the city.
- By Mark H. Friday
- Apr 01, 2017

Drone manufacturer, DJI, proposes that drones continually transmit identification.

The live webpage will frequently update with content from the show floor.
- By Matt Holden
- Mar 23, 2017
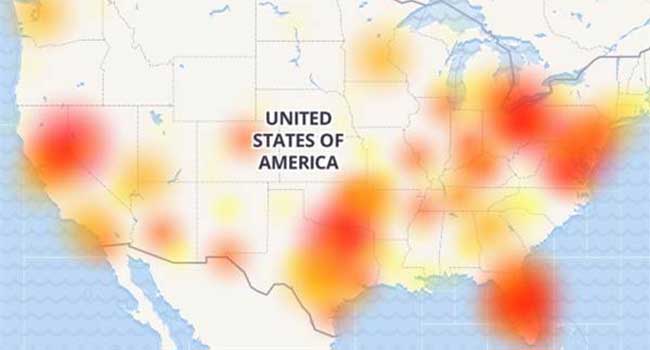
Users of AT&T’s wireless network found themselves without the ability to call 911 last night.

Mass-market drones have exploded in popularity over the last few years, with smaller price tags allowing thousands of hobbyists to purchase their own. From casual flyers to news organizations, the rising number of drones (UAVs) flying overhead brings serious security concerns with it.
- By Logan Harris
- Feb 16, 2017

Local, federal, state and private security officials are teaming up to create a security stronghold that protects a three mile area around the stadium.

This year marks the 20th anniversary of the world’s first IP network camera, a technology that eventually revolutionized the video surveillance landscape.
- By Fredrik Nilsson
- Dec 01, 2016

If these technologies aren’t on your radar, they probably should be. These product categories are rapidly growing in popularity and for good reason.
- By Brian Carle
- Dec 01, 2016
It’s an exciting time to be in the security industry, as evidenced by the successful year we have seen in regards to technology innovations, mergers and acquisitions, and a renewed sense of pride in the industry.
- By Sharad Shekhar
- Dec 01, 2016

What’s ahead in 2017? In 2016, we saw video surveillance and security increasingly become the focus of mainstream media conversations, with video playing a pivotal role in bringing terror suspects to justice (as it did recently in NYC) and with police body-worn cameras capturing sometimes controversial incidents that spark national conversations.
- By Wayne Arvidson
- Dec 01, 2016

Google announced their new method of two-step authentication, quite possibly the easiest way to log into an account.
- By Sydny Shepard
- Jun 23, 2016

A security firm was able to hack into Mitsubishi Outlander PHEV through its mobile app and disable the theft alarm.
- By Sydny Shepard
- Jun 08, 2016
A security flaw in Facebook’s Messenger platform allowed hackers to edit conversation and implant malicious links.
- By Sydny Shepard
- Jun 07, 2016

By definition, PIAM is an end-to-end solution that manages identities, compliance and events across disparate physical security systems.
- By Don Campbell
- Jun 03, 2016