When it comes to protecting transportation hubs, seaports have their own set of challenges.
- By Anthony Incorvati
- Feb 01, 2017

Earlier in 2016, when Gartner analysts stated that by 2020, 80 percent of all software will be offered on a subscription basis—this did not come as surprise to us at Genetec.
- By Christian Morin
- Feb 01, 2017
Financial institutions have been historically slow to adopt IP video surveillance citing concerns about possibly compromising network security.
- By Stephen Joseph
- Feb 01, 2017
Security threats are on the rise and as IT security teams increase their scrutiny of all network-connected devices, it’s time for some new thinking about the design and maintenance of building security systems.
- By John Szczygiel
- Feb 01, 2017
Based in Milwaukee, Wisconsin, Bell Ambulance Company has been in operation since 1977, growing into the largest provider of ambulance services in the state. The company responds to around 75,000 calls per year and provides a range of services.
- By Fernando Pires
- Feb 01, 2017

In 2015, an ex-deputy shot and killed an unarmed black man.

On Friday, January 27, President Trump signed an executive order that excluded travel from seven countries.

A group of gunman entered a mosque in Quebec and open fired killing six.
Company Leads Change in Customer Interaction with Home Security Providers

Governor Greg Abbot announced the funds would be given to the police department so they could outfit officers with new helmets, bullet proof vests.

Philadelphia is stepping up security as President Trump arrives for the GOP Retreat.

A draft order outlining many things including the revival of torture was published Wednesday.

President Trump is expected to sign two executive orders on Wednesday relating to border security.
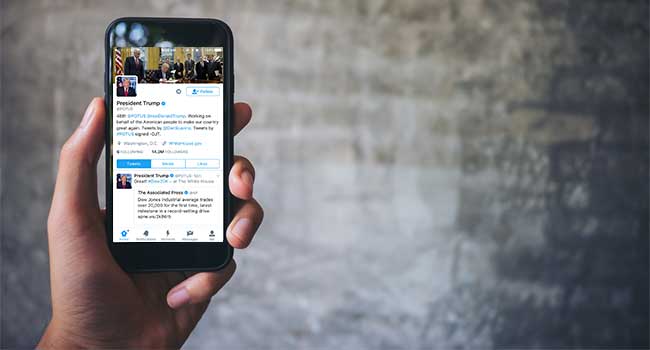
A hacker just wants President Trump to change his security settings on Twitter.
IDIS will mark two decades of innovation with customer, partner, and media events and recognitions across the globe in 2017
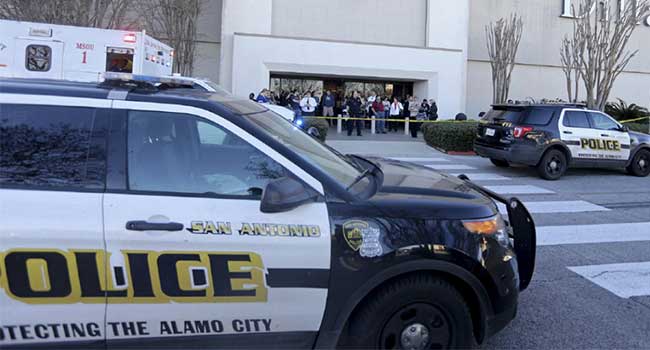
San Antonio police describe the event as a robbery gone, “really wrong.”

Security for the Inauguration is tight as protests swarm and a new president is sworn in.

Washington D.C. Police along with Secret Service and the FBI have been working to secure the Presidential Inauguration for over a year.