Act now and receive a special ISC West offer of $50 off the Certified Security Project Manager (CSPM) exam fee using discount code: 50ISCW2015.
Looking forward to serving customers and exceeding their expectations.
UHD video wall processor offering up to 4K resolution I/O, single wire connectivity and fully scalable windows.

Announced in a statement of two paragraphs totaling less than 100 words.
- By Ginger Hill
- Feb 26, 2015
Provides parking industry with a total parking guidance solution including vehicle counting, space available digital LED sign displays and parking management software.

TSA blocked access to missing badge records post-investigation.
- By Matt Holden
- Feb 26, 2015
Fresno-based monitoring station maximizes community resources, combats false alarms at more than double efficiency of national average.
RFID tracking in the automobile industry and harsh industrial applications that can withstand exposure to moisture, flames, chemicals, pressure and torsion.
Enhanced eFlow Power Supply/Charger enables remote monitoring, reporting and the control of power or devices from anywhere.
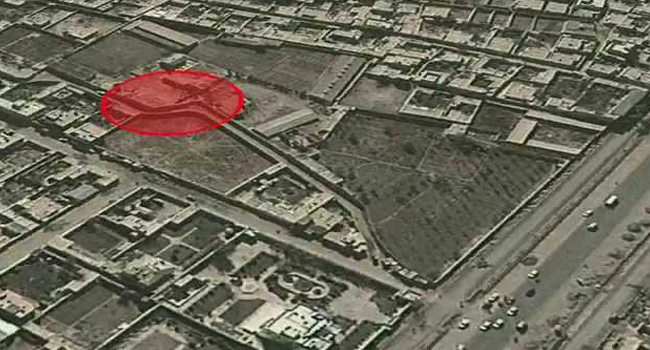
Mounting cameras on fixed-wing aircraft can provide more use data than police helicopters and for less money.

Like so many other large operations across the country, the mall is partially funded by Homeland Security.
- By Matt Holden
- Feb 25, 2015

Embarking on a remote video monitoring solution, especially third party, can seem like an overwhelming mission. However, with considerable value add to be gained by augmenting your security function, it’s imperative to educate yourself to recognize if it is right for you.
- By Cale Dowell
- Feb 25, 2015
Company to use proceeds to expand sales and marketing teams to respond to increased demand for its hyper-converged infrastructure products.

Just how safe will the "Internet of Toys" be for your children?
- By Ginger Hill
- Feb 24, 2015
Offers network video solutions for professional installations based on innovative and open technical platforms.
Delivers reliable, fiber-like performance via unlicensed wireless spectrum.
Sessions covering cybersecurity, proprietary platforms and unconventional security solutions to be offered on April 14 in Las Vegas.

A gunman opened fire at a restaurant in the Czech Republic, killing eight people before fatally shooting himself
- By Matt Holden
- Feb 24, 2015