
The nation is on high alert after a number of violent incidents.
- By Matt Holden
- Oct 14, 2015

The MP5000 portable crash barriers were used during Pope Francis’s visit to the U.S.
- By Matt Holden
- Oct 08, 2015

It’s not every day the Pope shows up for a visit, but when he does arrive in the United States, security is in the front of everyone’s mind.

Border Patrol agents assigned to the Rio Grande Valley Sector seized more than 1,400 pounds of marijuana Monday.

Ahmed Mohamed was detained after his teacher notified authorities.
- By Matt Holden
- Sep 16, 2015

Federal Authorities are concerned about security threats against the pope.
- By Matt Holden
- Sep 14, 2015

One man tried to find out.
- By Matt Holden
- Sep 10, 2015
Rewards invention and commercialization of anti-terrorism technologies.

A brief history of unsuccessful attempts in light of current presidential debates between candidates.
- By Ginger Hill
- Sep 01, 2015

With four or more access points around your property, there is no way that you can keep eyes at all entry points, especially if all can’t be viewed from a single location.
- By Scott Lindley
- Sep 01, 2015

Recreational drones could be used by adversaries to attack the United States.
- By Ginger Hill
- Aug 04, 2015

In recent years, the cruise industry has received a lot of attention from the news media regarding serious security issues onboard its vessels, ranging from people falling overboard to sexual assaults.
- By Jumbi Edulbehram
- Aug 01, 2015

Damarias Cockerham passed through the TSA checkpoint and boarded a flight to Guatemala.
- By Matt Holden
- Jul 29, 2015
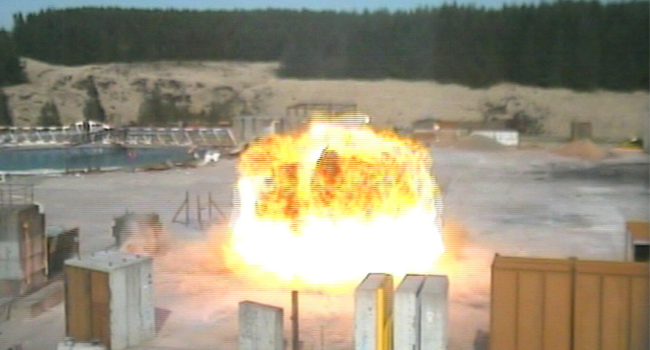
Tim Kempster, Wrightstyle’s MD, takes a look at bomb blast safety.
- By Tim Kempster
- Jul 22, 2015

The order covers thousands of military facilities within the U.S.
- By Matt Holden
- Jul 21, 2015

The threat of terror, real or imagined, has focused the minds of building owners, architects, engineers, technologists and planners to better design buildings that can withstand a whole new array of risks.
- By Lee Coates
- Jul 13, 2015

10 people arrested over the past 4 weeks.

Critics have said the law might be used to eliminate dissent.
- By Matt Holden
- Jul 01, 2015

Tips to help you, your family and friends stay safe and alert while enjoying firework displays.
- By Ginger Hill
- Jun 30, 2015

Gulf Arab countries face rising tensions due to conflicts between Sunnis and Shiites.
- By Matt Holden
- Jun 29, 2015