
Wireless technology in the security space is on the cusp of becoming the new norm. For the past few years we’ve seen the adoption of the technology grow steadily as it continuously improves upon traditional security solutions.
- By Peter Boriskin
- Oct 01, 2018

A key trend for 2018 has been the integration of AI with various security systems. AI-enabled surveillance cameras, facial recognition software, and fingerprint authentication scanners are just a few examples.
- By Yaron Zussman
- Oct 01, 2018
Cloud technologies are giving people access through their mobile phones and other devices to a variety of new experiences, while making their workplaces smarter and more data-driven.
- By Hilding Arrehed
- Oct 01, 2018
With the added video capabilities, Manteno authorities can alert agencies north or south of town to be on the lookout for specific vehicles with good description details.
- By Courtney Dillon Pedersen
- Oct 01, 2018

Northwestern Mutual operated several disparate security systems for access control, alarm management, intercom, video and visitor management. The new building project provided an opportunity to upgrade the security system and overall security program.
- By Kim Rahfaldt
- Oct 01, 2018

By their very nature, terrorist attacks are unpredictable and predicated on surprise. Staying one step ahead by identifying vulnerable areas, and securing them, is critical to staving off vehicular attacks.
The TSA is implementing some pretty amazing technology in order to improve explosives detection. In late August, the agency unveiled a state-of-theart advanced technology computed tomography (CT) checkpoint scanner for screening passengers and their baggage.
- By Ralph C. Jensen
- Oct 01, 2018
Good business is about partnerships. Our cover story in this issue comes from Jeff Huggins who has written about different examples of not only keeping people secure, but also offering protection.
- By Ralph C. Jensen
- Oct 01, 2018

The hack dates back to April 2018, and compromised information includes email addresses and passwords.
- By Jordan Lutke
- Sep 28, 2018

“Firefox Monitor” will allow users to check whether their personal information and passwords have been part of a data breach
- By Jordan Lutke
- Sep 28, 2018

The terminal will be deployed at Hartsfield-Jackson Atlanta International Airport, and will allow travelers to use facial recognition instead of their passports to pass through checkpoints at the airport.
- By Jordan Lutke
- Sep 28, 2018
Another busy day of GSX 2018 is in the books and with it came excited conversations, innovate products and streamlined solutions. With each booth I visited, I was excited by the new solutions and the potential deployments in the security space.
- By Sydny Shepard
- Sep 27, 2018
So, it all comes down to this. Today is the final day of the new GSX 2018, and the final tally should show a mixed review.
- By Ralph C. Jensen
- Sep 27, 2018

MacOS Mojave shipped with a bug that allows unauthorized access to a user’s private data.
- By Jordan Lutke
- Sep 27, 2018
Each year at trade shows I like to identify common theme. Usually, I base this off of the conversations that I have in different booths throughout the the show. For GSX 2018, I talked with several companies who are in the business of working smarter, not harder. The kinds of buzz words I heard were: intelligent, artificial intelligence, smart, deep learning and machine learning.
- By Sydny Shepard
- Sep 26, 2018
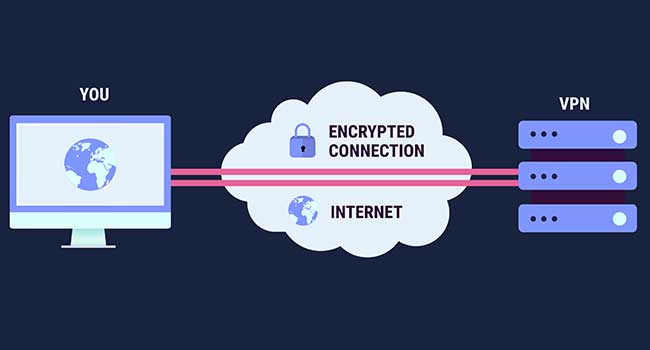
Understanding the details and the primary difference between free VPNs and paid ones.
Another busy day of GSX 2018 is in the books and with it came excited conversations, innovate products and streamlined solutions. With each booth I visited, I was excited by the new solutions and the potential deployments in the security space.
- By Sydny Shepard
- Sep 26, 2018
In its continued vision to innovate for a smarter, safer world, Axis Communications announced a new innovation for discreet corner surveillance and its latest innovations in bullet cameras and multidirectional cameras will be showcased at the Global Security Exchange (GSX) tradeshow in Las Vegas, NV, September 25-27.