
The President's national security team is looking at options to counter the threat of China spying on U.S. phone calls.
- By Sydny Shepard
- Jan 31, 2018

Japanese bitcoin exchange, Coincheck, is inspecting its cryptocurrency exchanges following $534 million theft.
- By Sydny Shepard
- Jan 30, 2018

Strava fitness app included a heat map of movement in their newest application upgrade which could be used against military bases.
- By Sydny Shepard
- Jan 30, 2018

Negotiations begin next month, and union leaders will also bring a request for panic buttons on behalf of the more than 14,000 housekeepers working on the Strip and in Vegas' downtown area. The goal of the wireless devices, which alert managers if workers are attacked, is to prevent sexual assault.
- By Jessica Davis
- Jan 29, 2018

Facebook as hired a former White House official as its first head of cybersecurity policy.
- By Sydny Shepard
- Jan 26, 2018
Smartphone application to help with security efforts during the Super Bowl.
- By Sydny Shepard
- Jan 26, 2018
CSLS now offers a product contest for safety and security products found on campuses.
- By Sydny Shepard
- Jan 25, 2018

According to a report released by Norton, hackers stole $172 billion from overconfident consumers in 2017.
- By Sydny Shepard
- Jan 25, 2018

Two students were killed and 14 others were shot at Marshall County High School.
- By Sydny Shepard
- Jan 24, 2018

Every year, we pause on January 28 to focus on data privacy and protection for the annual International Data Privacy Day.
- By Jason Cronk, Jessica Walton
- Jan 24, 2018
New System Health Monitoring Software Enables Faster Resolution Than Ever
Program incentivizes resellers to market and sell Razberi ServerSwitchIQ appliances with the CameraDefense cybersecurity solution

The convenience store of the future has some hefty security.
- By Sydny Shepard
- Jan 23, 2018

Two IEDs detonated at Eagle Ridge Mall in Lake Wales, Florida.
- By Sydny Shepard
- Jan 23, 2018
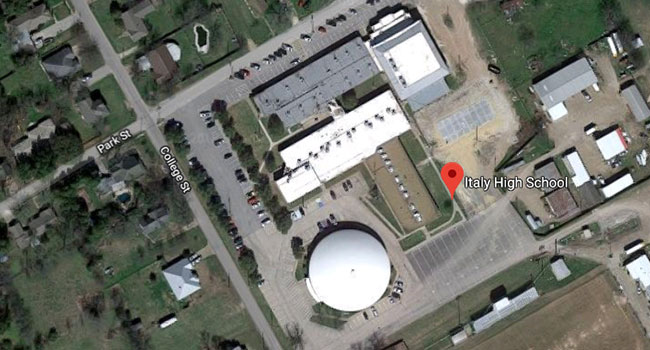
A male student shot and wounded a female student in the cafeteria of Italy High School in Italy, Texas.
- By Sydny Shepard
- Jan 22, 2018
Featured Solutions Deliver More Power, Versatility and Range

In just a few weeks, the Super Bowl will kick off after two years of planning the safety and security of the event.
- By Sydny Shepard
- Jan 19, 2018