
HID, a provider of trusted identity and physical security solutions, recently announced its inaugural State of the Security Industry Report, which gathered responses from 2,700 partners, end users, and security and IT personnel across a range of titles and organization sizes representing over 11 industries.
A highly integrated, data-driven approach to securing and managing major special events is driving cities to adopt innovative video technologies for safety and security.
- By Jason Tyre
- Mar 23, 2023

It is February 2014. A woman is getting ready in her room on a cruise ship when she hears a knock on the door; it is a crewmember delivering breakfast. She is not presentable so she tells him to leave it by the door.
- By Brian Davidson
- Mar 23, 2023
Providing real-time threat detection, insightful forensic searches, and long-term video archiving, Evolon Insites is delivered by securely connecting customer-premise video systems to powerful cloud-based analytics and video storage.
Amid global expansion, the security technology manufacturer Paxton has announced the appointment of Steve Taylor to their leadership team, as the company’s new CTO.
In recent years, there has been a significant increase in companies introducing AI technologies for the security surveillance industry. All are promising the ability to deliver some new capability or a better “mousetrap.”
- By Nick Israel
- Mar 22, 2023

Technology within the security industry has adapted to numerous changes through the years, from the early days of analog devices to today’s IP-based solutions, networked cameras, and access control solutions, in addition to analytics, cloud-based products, virtual security guards, and more.
- By Bruce Czerwinski
- Mar 22, 2023

Airport security is a complex system that incorporates multiple technologies to ensure the safety and security of travelers, employees and the facility itself. Sound-based technologies are integral pieces of this system, providing means of communication, notification and monitoring.
- By Cameron Javdani
- Mar 22, 2023
You have noticed and read the news, chaos and disruption, society veering away from the norm. At least the normal that was familiar to us. Without focusing on the grim reality of mass shootings, there is another crazy thing happening.
- By Ralph C. Jensen
- Mar 22, 2023
Allied Universal® has announced that it has formed a Global Program Management Office to manage Allied Universal Technology Services customer engagements worldwide. Mark Hauck has been promoted to the position of vice president of Global Programs to lead the initiative.

It was three years ago right about now that COVID was bringing the world to its knees. In mid-March of 2020, the president put travel restrictions on all flights in and out of Europe, the NBA suspended its season, and Tom Hanks announced that he’d tested positive for the disease—all in the same night. It was officially a national emergency two days later.
- By Matt Jones
- Mar 21, 2023

ISC West 2023 is right around the corner! This year’s trade show is scheduled from March 28–31 at the Venetian Expo in Las Vegas, Nevada. The Campus Security & Life Safety and Security Today staff will be on hand to provide live updates about the security industry’s latest innovations, trends, and products.
- By Matt Jones
- Mar 21, 2023
Award-winning global security leader, Gallagher, is excited to announce that Melissa Vidakovic has been named marketing director for the Americas. Melissa joins Gallagher with nearly 20 years of marketing experience in technology and software for companies across North America.
We all continue to see common themes across the headlines: Economic downturn, cross-industry job cuts and global geopolitical uncertainty. For businesses around the world, the turbulent situation can create unintended gaps in critical systems or processes that are core to operations.
- By Luke Tenery, Nathan Fisher
- Mar 20, 2023

A short three years ago we were all pondering whether to attend any tradeshows all thanks to COVID-19. Sorry to bring that nightmare up again, but it seems that little pandemic is in the rear-view mirror, and it’s time to meet again.
- By Ralph C. Jensen
- Mar 20, 2023
St. Louis-based Will Electronics is pleased to welcome, Ted Serve to its team as an account manager. He brings two decades of strong sales experience in the commercial security industry.

The International Security Conference (ISC), in collaboration with premier sponsor Security Industry Association (SIA), announced five of this year’s ISC West Keynote Series speakers. ISC West will kick off its annual conference on March 28 (SIA Education@ISC: March 28-30 | Exhibit Hall: March 29-31) at the Venetian Expo in Las Vegas, Nevada.
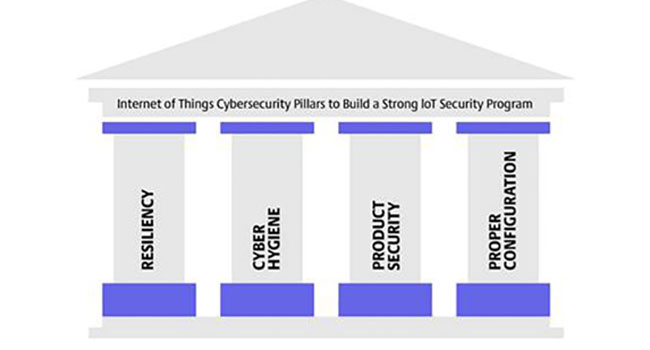
For our second pillar about the Industrial Internet of Things (IIoT) Pillars of Security, we are going to discuss what cyber hygiene looks like for IoT devices.
- By Will Knehr
- Mar 17, 2023