
President Trump has signed an executive order to strengthen the government’s cybersecurity.
Company adds Item Management to its HID Location Services and launches new HID Condition Monitoring Services that analyze equipment performance and health

The Transportation Security Administration has laid out new framework to protect soft targets in airports as well as consider electronics ban on flights from Europe.

Last night, President Trump abruptly fired FBI Director James Comey.
Sielox LLC, a leading provider of access control solutions since 1979, is pleased to announce the hiring of Jon VanDiver as its new Eastern Regional VP of Sales.

Passengers set to board a Spirit Airlines flight quickly gave into their air rage when the flight was cancelled.

Just days ahead of the French Presidential Election, candidate and now France’s president-elect announced his campaign had been hacked.

Chicago is overhauling their aviation security protocols after the viral incident involving an overbooked United flight.

It’s time to take the pledge to improve your password habits.
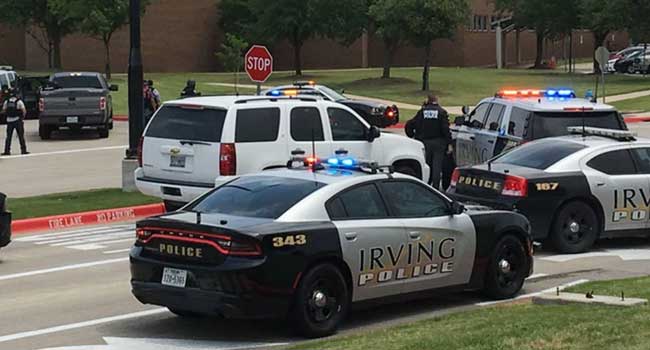
A man took his own life after shooting and killing a woman at North Lake College in Irving, Texas.

Don't edit that Google Doc, at least not today.
Siklu, the market leader in millimeter wave radios, has announced today the appointment of Eyal Assa as new CEO of the company.
Patrick Cuddy and Trevor Gardner to Lead Northeast Regional Sales Efforts

Dallas PD and first responders received a call about a suicide; the shooting spree that unfolded leaves many questions to be answered.

The suspect was taken into custody.

The upscale apartment complex is located near the University of California San Diego campus.
Winners to receive two of only 10 scholarships awarded industrywide
IDIS technology installed in more than two dozen office and storefront locations in multiple cities, delivering improved operational security through a comprehensive, state-of-the art video surveillance solution
Hospitals and medical centers face a number of challenges related to ensuring a safe environment for patients, staff, and visitors.
- By Greg Smith
- May 01, 2017

On Dec.19, 2016, the news exploded with information about a vehicle attack on a Christmas market in Berlin that killed at least 12 people and injured over 50 more.
Thirty-seven percent of people in the United States bought one or more smart devices in 2015, and many of the people in this large consumer market are tech savvy – so how do you tap into them? Having a broad online presence with positive messaging can help take your business to the next level. But, you may ask, “How do I get started?”
- By Lindsay Lougée
- May 01, 2017
The IT approach to layered security for systems, infrastructure and data is increasingly impacting the security department, and with good reason.
- By Jeff Whitney
- May 01, 2017
I admit there is not a lot in common between ballet and a security installation.
- By Ralph C. Jensen
- May 01, 2017

While these unmanned aircrafts are mostly used professionally and recreationally to add depth and intrigue to films and videos, security teams need to be aware of the threats they could pose on those below.
- By Sydny Shepard
- May 01, 2017

The proliferation of networked devices has increasingly brought IT to the table when discussing physical security.
- By Don Campbell
- May 01, 2017
By fully identifying and mitigating the practices which leave businesses vulnerable—and then investing in employee awareness training—you’ll greatly reduce risk while cultivating a more educated workforce.
- By Michael Marriott
- May 01, 2017

Integration of security systems is more than a concept or plan for Jeff Comeaux. It has become a passion and a calling.
- By Ralph C. Jensen
- May 01, 2017
Today, the God’s Love team relies on the Security Center unified platform to make sure that operations are running smoothly and that people are safe.
- By Andrew Elvish
- May 01, 2017
Hacking has become a threat far bigger than most think. Indeed, the greatest threat to national security these days comes from not from aircraft carriers or infantry divisions, but a computer with a simple Internet connection located anywhere in the world.
- By Scott Lindley
- May 01, 2017