
The President of the United States calls for stricter gun laws in the wake of the attack on San Bernardino.
- By Sydny Shepard
- Dec 07, 2015

Committee afraid for the safety of the President after reporting United States Secret Service downfalls.
- By Sydny Shepard
- Dec 04, 2015

Officials review protocols and take steps in a new direction following recent events with mass shootings.
- By Sydny Shepard
- Dec 04, 2015
Hidekazu Suzuki simultaneously named Senior Vice President
FBI able to confirm they are now "investigating these horrific acts as an act of terrorism."
- By Sydny Shepard
- Dec 02, 2015

Ensure that your front porch isn’t a victim of “porch piracy” with these 3 simple holiday package tips.
- By Sydny Shepard
- Dec 02, 2015

The Chapel Hill university warned students and staff to stay inside after reports of an armed and dangerous person.
- By Sydny Shepard
- Dec 02, 2015
BEI Security introduces new product at the Hi-Tech Defense Industry Fair.

VTech has been hacked putting the personal information of millions of people, including children, at risk.
- By Sydny Shepard
- Dec 01, 2015

The debate of security over privacy heats up after Paris attacks.
- By Sydny Shepard
- Dec 01, 2015

Video surveillance technology has come a long way from the days when analog CCTV cameras dominated the market.
- By Scott Schafer
- Dec 01, 2015

Traditionally, electrical substation security was aimed only at preventing access to stop vandalism and improve safety. Today, however, security efforts have been redefined to address new threats in order to protect critical infrastructure.
- By Reinier Tuinzing
- Dec 01, 2015
The video surveillance and physical security industry has been anything but quiet recently. Consolidation via merger and acquisition activity, competitive pressures driving costs lower and technology evolution are forces affecting trends both now and into the future.
- By Brian Carle
- Dec 01, 2015

When I’m asked what role access control devices and technologies play in a structure’s overall sustainability, my thoughts usually wander first to LED lighting.
- By Aaron Smith
- Dec 01, 2015

In the weeks following the massive explosion at a warehouse owned by Ruihai International Logistics in the Chinese port of Tianjin, investigators are getting a better idea of what led to the disaster that killed 173 people—104 of whom were firefighters—and injured hundreds more.
- By Glenn Trout
- Dec 01, 2015
By year’s end we have seen tons of new products and technology, and it amazes me that there is even more on the horizon.
- By Ralph C. Jensen
- Dec 01, 2015

Providing security for a house of worship wasn’t on my radar until recently. Dylann Roof changed all that when he opened fire on the Emanuel African Methodist Episcopal Church in downtown Charleston, S.C.
- By Ralph C. Jensen
- Dec 01, 2015
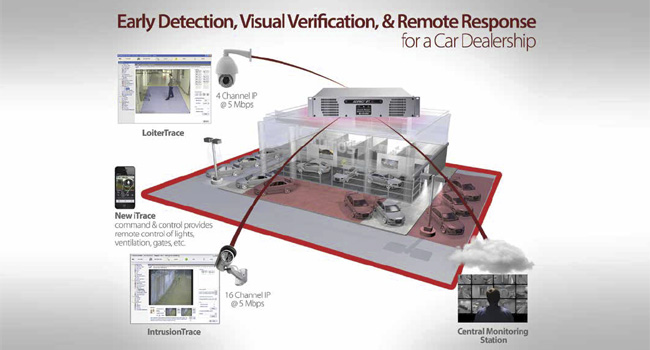
Car dealerships present a complex security challenge because they stock high-end models for the public to see, placing high-value assets out in the open where theft and damage can occur.
- By Katie Merluzzi
- Dec 01, 2015

For the highest level of security possible, Paramount chose to invest in enterprise command center software (ECCS) by SureView Systems to consolidate all of its security and life safety systems across the globe in a simple, effective and centrally manageable security management solution.
Total Recall is the video surveillance integrator for the Statue of Liberty

France ensures the safety of world leaders arriving in Paris for the COP21.
- By Sydny Shepard
- Nov 30, 2015
A shooting at a Colorado Springs Planned Parenthood leaves three dead and nine wounded.
- By Sydny Shepard
- Nov 30, 2015
FLIR Systems, Inc. announced today that it has acquired DVTEL, Inc., a provider of software and hardware technologies for advanced video surveillance, for approximately $92 million in cash.

The U.S. has issued a worldwide travel alert for Americans amid concerns that terror groups and individuals plan more attacks after the Paris massacres.
- By Sydny Shepard
- Nov 24, 2015
Kathleen Schraufnagel, Industry Liaison for Monitronics was chosen as the newest member to join the IQ Certification Board.

Airports’ busiest travel days of the year are likely to become even more complicated for travelers flying through U.S. airports this Thanksgiving Holiday.
- By Sydny Shepard
- Nov 23, 2015
STANLEY Security and I-View announce their partnership for live, actionable verified alarm response system.

Minneapolis police put together a guide to recognizing an attack before it happens.
- By Sydny Shepard
- Nov 23, 2015

We may have finally found a more efficient way of getting through airport security.
- By Sydny Shepard
- Nov 21, 2015

Fifth Third Bancorp, one of the top 15 banks in the U.S., is well on its way toward completing a major upgrade of its video surveillance system.