As a provider of storage for video surveillance systems, the hardest part of my job is educating end-users, integrators and consultants on the best way to purchase storage for their systems.
- By Scott Seraboff
- Apr 01, 2017
The thought of a network or individual cameras getting hacked brought cybersecurity into the security picture pretty quickly. Cyber questions also arise when discussing cameras being manufactured in China.
- By Ralph C. Jensen
- Apr 01, 2017
Three years ago, Shrader Engineering had the privilege of designing one of the most unique security concepts in the region for the city of Sugar Land, Texas, Police Department. The security system forms a “virtual gateway” throughout the city.
- By Mark H. Friday
- Apr 01, 2017

The large geographical area and variety of locations and assets to protect make municipal video surveillance particularly challenging.
- By Ken LaMarca
- Apr 01, 2017

Glendale and Phoenix security officials feel confident in the security plan that will form around the men’s basketball tournament.
Clay Solutions B.V. has announced the release of Clay Locking Platform – the only API that makes it possible to integrate cloud-based access control to existing businesses and product portfolios.
SALTO Systems, a leading manufacturer of electronic access control solutions, has appointed Adam Reed to the commercial sales team position of Western Regional Sales Manager.
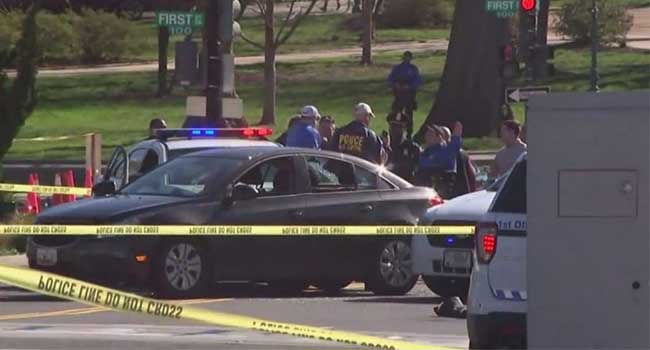
Shots were fired when U.S. Capitol Police tried to stop an erratic driver on Wednesday morning.

To improve customers’ entrance experience, Magic Kingdom is pushing their security checkpoints outside the transportation and ticket center.
Two new VP and Director positions and four significant internal promotions and appointments jump-start Milestone in 2017
Panasonic announced that its Panasonic Security Business Group has formally integrated the company’s security camera and related devices business with the business of Video Insight.

Drone manufacturer, DJI, proposes that drones continually transmit identification.

Occly™ is a wearable personal safety device worn on the body or clipped to an accessory.
After a successful inaugural run in 2016, the Connected Security Expo is back for year two at ISC West 2017 with some important changes.
- By Brent Dirks
- Mar 28, 2017

Britain police are looking to review security efforts around Parliament after a vehicle and knife attack that killed four people.
Take a walk around the show room floor, talk with those you do business with and post on social media!
- By Sydny Shepard
- Mar 27, 2017

Police are not investigating this incident as terrorism.

If there is anything I’ve learned in my one year at ISC West it’s how to pack for the event.