
November 2015
- Protect Your Data
- Winning a Better Solution
- Advanced Considerations
- Define New Models
- Tight as a Drum
- Keeping Your Customers Secure
Features

Network Communications are integral part of new security systems
By Ronnie Pennington
Now is an exciting time to be in the business of security integration. The quality of surveillance images are getting better in a variety of configurations ranging from megapixels to multisensor panoramic to thermal imaging cameras.

Installing a product that will grow with the firm
By Scott Lindley
In the decade that First Service Insurance (FSI) has conducted business in Roseville, Calif., it has provided contractors with specialized property and casualty insurance products focused on general liability, workers compensation, business auto and bonding/surety.

Technology offers a variety of peace of mind benefits
By Juan M. López
As interest in connected home technology rises, consumers are beginning to pay attention to its many safety and security benefits.

Protect your assets with a complete security plan
By Denny Heaberlin
In the minutes, hours and days that follow a widespread, widely publicized data breach, most companies scramble to increase their security measures in an effort to overcompensate for their lack of proactive preparation.

Bicycle shop seeks user-friendly access control to protect valuable trade secrets
By Taylor Foster
There are many challenges associated with securing Specialized including theft protection and loss prevention, general security for employees, and protecting the company’s highly confidential trade secrets which are safeguarded at headquarters.
Human process is painstakingly slow
By Steven Pisciotta
Employee mustering at industrial sites or large facilities has typically been difficult to efficiently manage due to the complexity of the situation and human factors.

Enhanced security, with a padlock?
By Ryan Baer
Imagine getting slapped with a $1 million fine for not adequately securing your facility. Think it can’t happen? Think again.
Departments

Industry Vertical
By Mohammed Murad
At the peak of El Salvador’s sugar harvesting and processing season, the Ingenio Azucarero Injiboa mill in San Vicente becomes incredibly busy as hundreds of employees change shifts throughout the entire day, typically seven days a week.
Industry Professional
Integrators and users benefit from network intelligence
By Ralph C. Jensen
Security Products magazine sat down with Larry Ye, president and CEO of LifeSafety Power Inc., to discuss how rapid transformation is occurring in the technology—and how RMR is now possible, providing value to both systems integrators and their end-user customers.

Industry Focus
By Ralph C. Jensen
More than a decade ago, the talk was all about convergence. Well, the industry has converged, but there is now something more interesting on the horizon.
Networking Security
A layered approach to security
By Michél Bechard
A layered approach to network security is the most reliable way of ensuring peace of mind against Advanced Persistent Threat (APT) forms of cyberattacks because no modern company can afford the surefire method of protection
Keeping the network secure helps protect Boston Marathon runners
By Ron Grinfeld
Realizing the need for stronger surveillance in high-profile locations such as the marathon route, the city of Boston decided to increase civilian protection. The new security measures included doubling law enforcement personnel to about 3,500, the addition of bomb-sniffing dogs, and a SWAT team provided by the FBI.

CIO and CSO see changes as information and facility security converge
By Brandon Arcment
Physical security administrators and IT departments have both gotten much more involved with each other in system deployment decisions, ever since video surveillance first began transitioning from analog to network cameras.

A new type of cyber-crime: From kindergarteners to adulterers
By Avner Mor
This privacy sensitivity occurred innocently in the physical world on a beautiful avenue. But, privacy sensitivity can be even more critical in the virtual world.

Tackling the end users’ security vulnerability
By Ryan Corey
As IT security professionals, we’re great at providing our clients with firewalls, encryption software and other technological safeguards against data breaches. But, did you know that even your best-protected clients may face an even greater threat than poorly managed networks and systems?
Dealer Strategies

Dealers can get a running advantage with the right technology, and the right training
By Ralph C. Jensen
When it comes to security and home automation, there are a lot of questions homeowners need to ask themselves. Do I want a smart home?
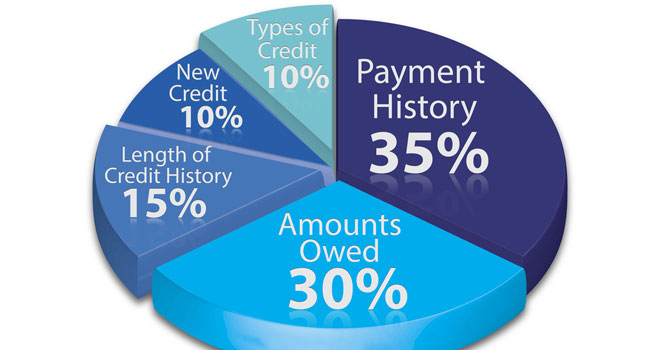
Credit counts in a balanced portfolio
By Robert Ogle
Most dealers know that it’s crucial to run a credit report before signing up a new account. But it’s also worth remembering that it’s not a minor detail, and even a borderline credit record may have long-term repercussions.
Editor's Note
By Ralph C. Jensen
This month I ventured out just a little bit to talk about residential security, though much of what I learned also applies to commercial and industrial security. No better place to learn about software than Silicon Valley.

Self-install with professional monitoring
By Bart Didden
According to several studies, growth is now focused on “self-installed” products that piggyback on the popularity of smart phones and the tech-savvy millennials that use these devices for everything from banking to prepared food delivery.
Campus Security & Life Safety

San Diego schools de-escalate incident and protect assets
By Courtney Pedersen
The San Diego Unified School District’s previous video surveillance solution presented a number of problems. It required two management servers in which most settings had to be replicated between the two, which was awkward and cumbersome.

Integration between event management, HR and resource-planning platforms form core of installation
By Mitchell Kane
Designed to a be a state-of-theart facility for students and faculty members at Oregon State University, Austin Hall could represent one of the most unique systems integration projects within the higher education market in the United States.
Editor's Note
By Ralph C. Jensen
This issue of Campus Security & Life Safety has an interesting take on security. I think I’ve taken it for granted, but when you talk about camera installation, you have to think about the lens for the camera.

Facility and IT security systems converge to manage security
By Brandon Arcment
Now that mobile identities can be carried on phones for physical security applications, they are merging with smart cards into centralized identity management systems.

Geutebruck helps secure Florida school district
By Ellen Kreitz
Vandalism and destruction of property are not the only concerns at schools. Sadly, theft, assaults and campus shootings are also important issues.
As emergency towers become ubiquitous across college campuses, the focus for many campus security experts shift from presence of product to quality of product
By Molly Walsh
One of the campus’s current projects is the renovation and expansion of the Rietz Student Union that prompted the discovery of several ‘dead zones’ in the outdoor notification program.

Video surveillance systems need the right glass to work properly
By Andrea Iniguez
This is a story of lens selection gone wrong, and right. Often it seems lens selection is not given much attention, and at worst is an afterthought.