Highly malicious strain found only takes 1 click to infect systems using DropBox.

One is dead and two are severely injured after guards opened fire
- By Matt Holden
- Mar 30, 2015
Complete, unified, end-to-end security solution to manage all security and complementary technologies in one place via an intuitive user interface.
Achievements in waste diversion and reductions in carbon footprint, energy demand and water use.
Specialized manufacturer supports NIR bandwidth for security and surveillance.
Company more than doubles its business with acquisition of Checkview.

Always listen and obey the guide; he or she is there to keep you safe and secure.
- By Ginger Hill
- Mar 27, 2015

In the aftermath of flight 9525, security officials are looking into cockpit safety practices.
- By Matt Holden
- Mar 27, 2015
Deterring robbery, employee theft or shoplifting top priority.
Integrated platform combines solar and wireless technologies to enable video surveillance in remote and challenging geographic locations.
SmartCode 916 Touchscreen deadbolt takes the honors in access control category.
Support on-board, advanced motion detection; image stabilization; and optional video content analysis with a full suite of rule-based filters.
In-line, high-speed hot stamping technology produces secure brand protection labeling solutions.
Upgraded system compatibility and new features added to KeyWatcher’s OnGuard access control system module.

The co-pilot locked the cockpit door once the pilot left to use the restroom.
- By Matt Holden
- Mar 26, 2015

Per Björkdahl shares his thoughts about cybersecurity, the IP video market, access control and interoperability.
This is the year that Pelco by Schneider Electric makes the data-driven, immersive surveillance system an effective reality.
Comes with a built-in, supervised, digitally-coded wireless transmitter, and visual and audible alarm with low battery indicator.
Integrated with entry system, long-range solution opens Kolea at Waikoloa Beach Resort.
March Networks GURU Smartphone App helps save time and money in the field.
Exploits many features that have made Cyton a successful CXP frame grabber by incorporating cost-effective, highly-compatible Camera Link interface.
Expanded BT200Z smart card reader includes support for Windows 8.1.
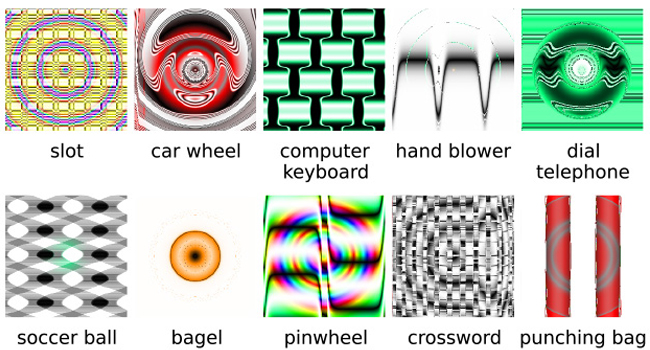
Machines learning to recognize objects with accuracy, but can also be fooled by optical illusions.
- By Ginger Hill
- Mar 25, 2015

The report says the FBI needs to hire more linguists to counter rapidly evolving threats.
- By Matt Holden
- Mar 25, 2015

Believed to be the largest dataset ever publicly released in the United States.
- By Ginger Hill
- Mar 24, 2015

A flaw was discovered in the Hilton HHonors program that could let anyone hijack all accounts.
- By Matt Holden
- Mar 24, 2015
High quality, vastness of feature set recognized as second to none in industry.
Cyber security and cyber space technology has become one of Israel's most important exports.
exacqVision combined solution improves loss prevention and retail analytics.
Customer-focused empowerment strategy to drive growth and enhance value to partners.