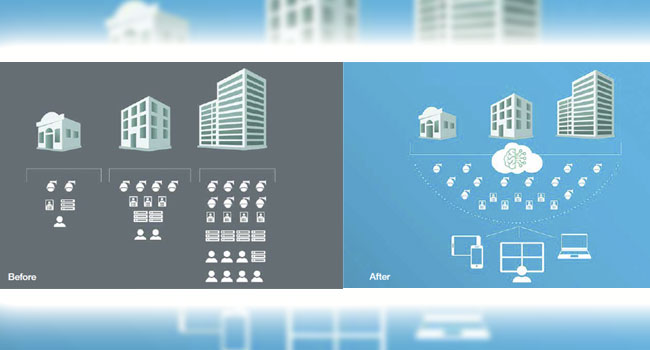
There’s enormous opportunity for all enterprises in the cloud, and those in the middle market are taking note.
- By Andreas Pettersson
- Feb 01, 2019

Originally designed as consumer devices, smartphones have become vital elements of both our personal and professional lives. Unfortunately, as sources and repositories of our most sensitive data, smartphones have quickly become a primary attack surface for hackers, cybercriminals and foreign spies.

College and university campuses aren’t immune from the same types of crime, such as burglary and assault, found in any small city where thousands of people live and work closely together. Yet overall, campuses remain a mostly safe place for young adults to learn and mature.
- By Paul Hefty
- Feb 01, 2019
When Paramount Studios, the longest operating and only remaining studio in Hollywood, wanted a preventative solution that would protect tourists and talent from car attacks, they contacted Perimeter Security Group, an integrator that has become one of the leading providers of perimeter security systems in the country.
The government has its fingers in everything, and it is necessary when you think about managing the nation’s infrastructure. Think carefully about securing the nation’s transportation system.
- By Ralph C. Jensen
- Feb 01, 2019
While attending religious services during the holiday season, a local congregant asked me if I had heard about the ISIS threat to local houses of worship in East Texas. I was not aware, but I started digging.
- By Ralph C. Jensen
- Feb 01, 2019

With all this plus four lobbies and multiple entry points, security at American Airlines Center is a 24/7 responsibility. Finding the right camera system for such a diverse environment presented a challenge.
- By Mark McCormack
- Feb 01, 2019
Everyone wants a piece of Kessel Run, the Air Force’s agile software development program, and attempts to replicate its success of are already underway.
- By Lauren C. Williams
- Feb 01, 2019

At JFK Airport, immigration officers process hundreds of international passengers per flight. With the continual influx of people combined with limited staffing, law enforcement personnel are increasingly looking for technologies to enhance their efforts to deter illegal entry or trafficking and aid in crime investigation.
- By Richard Brent
- Feb 01, 2019

The technology behind today’s optical sensors and lenses has come a long way in trying to mimic some of the hallmark characteristics of the human visual system.

As part of the preparations for next year’s summer Olympics in Tokyo, Japan’s National Institute of Information and Communications Technology will check about 200 million internet-connected devices for potential cybersecurity vulnerabilities.
- By Jessica Davis
- Jan 31, 2019

Philadelphia City Hall installed an X-ray machine and metal detector at its entrance during the holidays, according to KYW Newsradio 1060.
- By Jessica Davis
- Jan 31, 2019

Trustees’ spokesperson Tracy Davis said that at least one officer will be on duty during all times the library is open to the public. Davis said that the security schedules are coordinated to provide officer coverage for all 59 ½ hours of the library’s weekly schedule.
- By Jessica Davis
- Jan 31, 2019

The Supreme Court of Illinois ruled Six Flags Great America collected a boy's thumbprint without proper consent.
- By Sydny Shepard
- Jan 30, 2019

A glitch in Apple's FaceTime app let users hear—and see—the other person even if the recipient never accepted the call.
- By Sydny Shepard
- Jan 30, 2019
Hyperconverged infrastructure optimized with Genetec Security Center to enhance video capture in enterprise-class IoT and security environments

West Virginia city looks to install security cameras in places where power is limited.
- By Sydny Shepard
- Jan 29, 2019