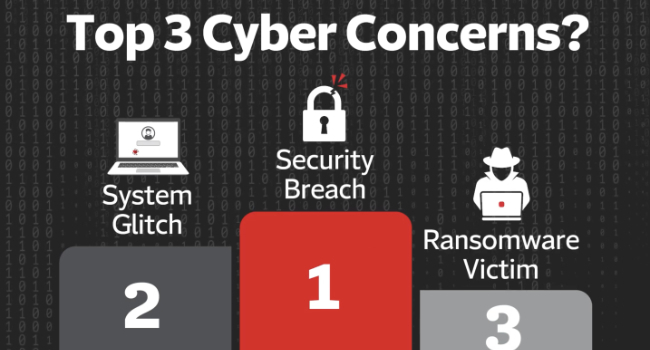
The Travelers Companies, Inc. recently released its 2022 Travelers Risk Index results, and for the third time in four years, the survey found that cyber threats were the top overall concern for business decision makers.
Hanwha Techwin, a global supplier of IP video surveillance solutions, today announced that it has integrated its intelligent IP cameras with Epic Systems' new remote sitting video platform called E-CAL.
I see and learn about myriad products that are about to or have recently hit the security market. The technology is amazing, but at the heart of every tradeshow are the people. As I made my way around the GSX show floor, I found some interesting products I wanted to share, and, I’ll share more in coming weeks.
- By Ralph C. Jensen
- Sep 27, 2022

Global Security Exchange (GSX) 2022 has concluded at the Georgia World Congress Center in Atlanta, Georgia. Presented by ASIS International, the world's largest association for security management professionals, the event offered discussion and idea exchanges for the global security community.

New York Gov. Kathy Hochul recently announced the Metropolitan Transportation Authority New York City Transit has received a $2 million award, through the Urban Area Security Initiative federal grant program, which will provide funding for the installation of cameras across the entire fleet of subway cars, enhancing security coverage, and, most importantly, increasing passenger confidence in mass transit safety.
Commvault has announced the general availability of Metallic® ThreatWise™ an early warning system that proactively surfaces unknown and zero-day threats to minimize compromised data and business impact.
Versa Networks has announced that Gartner, a company that delivers actionable, objective insight to its executive and their teams, has given Versa Networks (Versa Operating System VOS™) the highest score for the Large Global WAN Use Case, as published in the 2022 Gartner Critical Capabilities for SD-WAN report.
Smart buildings are essential building blocks within the complex smart city ecosystem as they contribute significantly to the sustainability of cities. Many governments’ visions of smart cities include not only making urban environments more sustainable.
- By Brent Jacot
- Sep 20, 2022
Gallagher has today announced an enhancement to their cloud-based security solution – added support for a wider variety of doors including gates, roller doors, and cabinets.
The Security Industry Association (SIA) has announced that it is developing a new apprenticeship program to help address the security industry’s workforce challenges, diversify the talent pipeline and foster career development opportunities within the industry.
RGB Spectrum® has continued its partnership with Lockheed Martin to equip F-35 flight simulators with its latest video processing technology.
Idesco Corp. is announcing an expanded offering to include comprehensive Visitor Management solution.

Organizations of every type and size often need to make informed decisions for areas of improvement, enhancement, and change.
- By Fabiola Ruvalcaba
- Sep 20, 2022
Camect Inc., a smart hub device is adding artificial intelligence detection to all ONVIF and RTSP security cameras.
The new world of AI-driven video analytics is a pattern recognition on a massive scale. Known actions and their corresponding reactions analyzed by software, and through the process of machine learning, provided with programs that can detect, analyze new and evolving patterns.
- By Amit Kumar
- Sep 20, 2022
Societal and economic conditions related to increases in operating expenses have created recruiting and retention challenges impacting all employers and increasing guarding costs over the past few years.
- By Jordan Lippel
- Sep 20, 2022

Significant innovations in key technology areas have enabled the development of jaw-dropping new video applications and handed a multitude of opportunities to a wide swath of business segments.
- By Brian Mallari
- Sep 20, 2022

Now that summer vacations have come to an end and the skies are getting dark earlier, it’s a good time for homeowners to take a look at their home’s security.
- By Wade Gibson
- Sep 19, 2022