
MacOS Mojave shipped with a bug that allows unauthorized access to a user’s private data.
- By Jordan Lutke
- Sep 27, 2018
Each year at trade shows I like to identify common theme. Usually, I base this off of the conversations that I have in different booths throughout the the show. For GSX 2018, I talked with several companies who are in the business of working smarter, not harder. The kinds of buzz words I heard were: intelligent, artificial intelligence, smart, deep learning and machine learning.
- By Sydny Shepard
- Sep 26, 2018
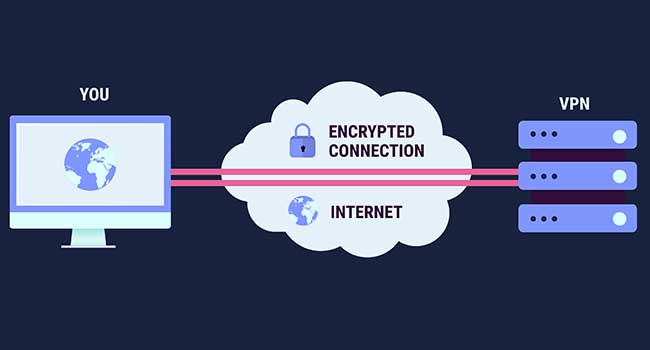
Understanding the details and the primary difference between free VPNs and paid ones.
Another busy day of GSX 2018 is in the books and with it came excited conversations, innovate products and streamlined solutions. With each booth I visited, I was excited by the new solutions and the potential deployments in the security space.
- By Sydny Shepard
- Sep 26, 2018
In its continued vision to innovate for a smarter, safer world, Axis Communications announced a new innovation for discreet corner surveillance and its latest innovations in bullet cameras and multidirectional cameras will be showcased at the Global Security Exchange (GSX) tradeshow in Las Vegas, NV, September 25-27.
It is not a secret that campus security is the buzz word around events like GSX given the on-campus violence we have seen in the last year. Companies are putting their heads together and trying to figure out a better way to keep students, faculty and staff safer at K-12, universities, medical facilities, corporate campuses and more.
- By Sydny Shepard
- Sep 26, 2018
There are plenty of great things to talk about when it comes to a security tradeshow; however, there may not be anything more important that people coming together for a common cause.
- By Ralph C. Jensen
- Sep 26, 2018
Viakoo, a provider of a proven means to proactively automate surveillance and access control system verification in the security industry, is demonstrating solutions to assist in proving and maintaining regulatory or organizational compliance at GSX 2018 (booth #2943).
It is easy to get lost in the midst of a large trade show, here are three tips to ensure you are getting the most from your trip.
- By Sydny Shepard
- Sep 25, 2018
OnSSI, an industry leader in Video Management Software (VMS) solutions, is publicly debuting the latest enhancements to its powerful Ocularis 5.6 VMS platform and new RecOn5 Pre-loaded NVRs and Servers here at GSX 2018 (booth #2263).
Motorola Solutions recently announced new features for Ally, its cloud-based security software platform for enterprises in North America. Available now, the enhancements enable communication and real-time information-sharing for security teams.
Dortronics, an industry leader in off-the-shelf and customized door control solutions, is showcasing the latest enhancements to its extensive product portfolio here at GSX 2018 (booth #714).
- By Ralph C. Jensen
- Sep 25, 2018
Boon Edam Inc., a global leader in security entrances and architectural revolving doors, is showcasing the company's continuing advances in technology and customer support in booth #1715 at the GSX (formerly ASIS) exhibition in Las Vegas, NV from September 25-27. With the launch of their new Interactive Troubleshooting Guides for Security Entrances, a range of new partner technology integrations and the growing adoption of anti-tailgating and anti-piggybacking entrances by Fortune 50 Global companies, the company is advancing its position as the market leader in the Americas in security entrance solutions
Altronix, the recognized leader in power and transmission solutions for the professional security industry, has enhanced the ACMS8 Dual-Voltage Access Power Controller with bi-color output LEDs to visually indicate 12VDC or 24VDC at-a-glance.
Morse Watchmans, the world leader in key control and asset management systems, is demonstrating the benefits of their KeyWatcher® Touch key management system at the GSX show (formerly ASIS) in Las Vegas from September 25-27.
Vidsys recently announced the release of its latest Converged Security and Information Management (CSIM) software platform, Vidsys Enterprise 2019 Release 1.0, enhancing the operator experience through the addition of the Synchronized Playback Studio.
Never miss a thing with Security Today's Live From GSX social zone.
- By Sydny Shepard
- Sep 25, 2018
Panasonic System Solutions Company of North America, a leading provider of connected security solutions for numerous verticals including law enforcement, transportation and educational institutions will showcase new additions to its diversified technology portfolio of end-to-end security and evidence management solutions at Global Security Exchange 2018 Expo (GSX), September 23-27 in Booth #2737 at the Las Vegas Convention Center in Las Vegas, NV.
Fire detection is reaching new, advanced levels, designed to help save more lives. Edwards, continuing in its legacy as the inventor of the alarm bell, is the first multi-criteria smoke detector manufacturer to receive certification to the UL standard for Fire Alarm Systems UL 268, 7th edition, set to take effect May, 2020.
Sielox LLC is showcasing the company's latest Advanced Access Control and Emergency Notification and Response solutions here at GSX 2018 in booth #3914.
DITEK, a leading provider of surge protection solutions, is displaying their newly improved DTK-RMNETS series of modular network protection products here at GSX 2018 (booth #3857).

You could be making yourself a prime target.
- By John Mason
- Sep 25, 2018
ISS - Intelligent Security Systems, a leading provider of intelligent VMS and analytics globally, is demonstrating its newly released SecurOS™ v.10 Video Management System supported by their powerful suite of native intelligent analytics, along with SecurOS™ Smart NVR, an all-in-one video management appliance here at GSX 2018 (booth #2151).

NYPD and federal, state and local law enforcement agencies will partner to provide thousands of highly trained officers to ensure safety throughout the city during the event. The police presence will include both uniformed and plainclothes officers.
- By Jessica Davis
- Sep 24, 2018

Alexa speakers are always listening; Alexa Guard will allow them to listen for the sound of broken glass or the sounds of smoke or carbon monoxide alarms. If heard, the system will then alert the user.
- By Jessica Davis
- Sep 24, 2018

Attackers injected 15 lines of Javascript code into Newegg.com’s web store, forwarding payment information to their own server.
- By Jordan Lutke
- Sep 24, 2018

Deputies were dispatched at 9:09 a.m. and arrived on the scene in five minutes, Gahler said. No shots were fired by law enforcement, and the woman died at a hospital nearby after shooting herself, he said.
- By Jessica Davis
- Sep 21, 2018

Five people were shot Thursday night at a residence in Syracuse, New York, authorities said. As of late Thursday, authorities hadn’t identified a suspect nor a motive, according to Police Chief Frank Fowler.
- By Jessica Davis
- Sep 21, 2018

At least 50 of the cameras will have license plate recognition capabilities, according to WBRC. The station also reported that the cameras should be able to work with Birmingham’s gunfire detection ShotSpotter system.
- By Jessica Davis
- Sep 21, 2018