
“The OVMC-EORH employees and medical staff have been very adaptive and supportive, and we are able to continue with quality patient care,” Ohio Valley Medical Center CEO Daniel Dunmyer said.
- By Jessica Davis
- Nov 29, 2018

Here are five principles that developers should keep in mind to create more secure apps
- By Madhan Kanagavel
- Nov 29, 2018

Tips and tactics for ensuring your small business is safe from the threat of cyberattacks.
- By Michael Flavin
- Nov 28, 2018
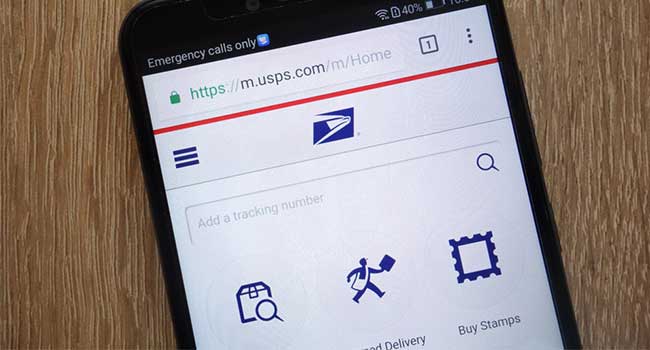
A security hole in a mail preview program may have made the data of 60 million customers vulnerable.
- By Sydny Shepard
- Nov 28, 2018

The German government has prosed guidelines to increase router security including what kind of routers are sold and installed across the country
- By Sydny Shepard
- Nov 27, 2018

How a 10-minute survey cost Facebook $150 billion
- By Colin Earl
- Nov 27, 2018

Internet connected devices might be the hot item for Christmas this year, but are they secure?
- By Sydny Shepard
- Nov 23, 2018

Recommendations for safe online holiday shopping - a cybersecurity perspective.
- By Sydny Shepard
- Nov 23, 2018
- By Tyler Reguly
- Nov 21, 2018

Beware holiday shoppers. Attempts at fraud will peak on Thanksgiving Day this year.
- By Sydny Shepard
- Nov 21, 2018

SUNY Upstate Hospital announced a former employee inappropriately accessed more than 1,200 patient records.
- By Sydny Shepard
- Nov 16, 2018

According to a Nordstrom spokesperson, no customer data was involved in the breach. In a statement, the company said it was “investigating an incident where a contract worker improperly handled some Nordstrom employee data.”
- By Jessica Davis
- Nov 15, 2018

A new cyberspace pact was signed by 51 other countries, 224 companies and 92 non-profits and advocacy groups.
- By Sydny Shepard
- Nov 14, 2018

To help you rule out the worst password ideas, FrontNet has put together a list of the 25 words passwords on the internet for 2018.
- By Jessica Davis
- Nov 13, 2018

In a privacy update on its site, the Ontario Cannabis Store said the breach affected about 2 percent of its customer orders, or 4,500 customers. Canada Post said customers’ information was accessed by someone using its delivery tracking tool.
- By Jessica Davis
- Nov 12, 2018

"HSBC became aware of online accounts being accessed by unauthorized users between October 4, 2018 and October 14, 2018," the bank wrote in a data breach notification letter submitted to Californian authorities.
- By Jessica Davis
- Nov 08, 2018

Researchers found a malicious expert can bypass existing protection mechanisms and access the data without knowing the user-chosen password.
- By Sydny Shepard
- Nov 07, 2018

It’s thought that the private message data was obtained via a malicious browser extension that scraped the data from users’ accounts. The hackers claimed to sell access to the information for 10 cents per account.
- By Jessica Davis
- Nov 06, 2018

Security firm Armis has discovered two vulnerabilities in Bluetooth Chips from several networking industry leaders.
- By Sydny Shepard
- Nov 05, 2018

Today, more and more video security cameras are increasingly connected to the internet and transitioning into intelligent sensors that collect significantly more data than video security images alone.