This is the year that Pelco by Schneider Electric makes the data-driven, immersive surveillance system an effective reality.
Comes with a built-in, supervised, digitally-coded wireless transmitter, and visual and audible alarm with low battery indicator.
Integrated with entry system, long-range solution opens Kolea at Waikoloa Beach Resort.
March Networks GURU Smartphone App helps save time and money in the field.
Exploits many features that have made Cyton a successful CXP frame grabber by incorporating cost-effective, highly-compatible Camera Link interface.
Expanded BT200Z smart card reader includes support for Windows 8.1.
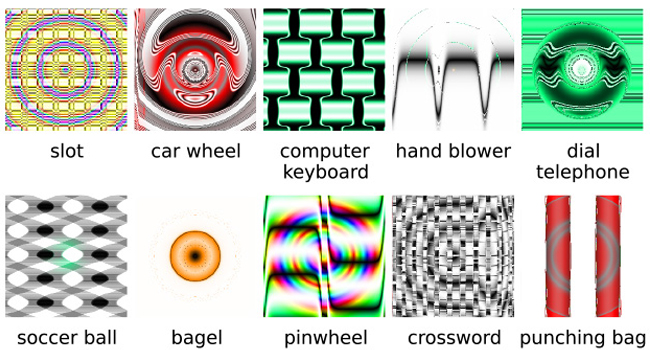
Machines learning to recognize objects with accuracy, but can also be fooled by optical illusions.
- By Ginger Hill
- Mar 25, 2015

The report says the FBI needs to hire more linguists to counter rapidly evolving threats.
- By Matt Holden
- Mar 25, 2015

Believed to be the largest dataset ever publicly released in the United States.
- By Ginger Hill
- Mar 24, 2015

A flaw was discovered in the Hilton HHonors program that could let anyone hijack all accounts.
- By Matt Holden
- Mar 24, 2015
High quality, vastness of feature set recognized as second to none in industry.
Cyber security and cyber space technology has become one of Israel's most important exports.
exacqVision combined solution improves loss prevention and retail analytics.
Customer-focused empowerment strategy to drive growth and enhance value to partners.
Executives to share insights on advanced identity technologies in conference sessions at connect:ID 2015.
Part of Indonesian Government's plans to boost annual passenger numbers beyond 60 million people.
Security industry professionals have opportunity to earn undergraduate or graduate degree.
Diverse product suite of access control readers and panels, facial recognition, IP and AHD cameras, elevator and floor access controllers, turnstiles and consumer products.