Hospitals and medical centers face a number of challenges related to ensuring a safe environment for patients, staff, and visitors.
- By Greg Smith
- May 01, 2017

On Dec.19, 2016, the news exploded with information about a vehicle attack on a Christmas market in Berlin that killed at least 12 people and injured over 50 more.

While these unmanned aircrafts are mostly used professionally and recreationally to add depth and intrigue to films and videos, security teams need to be aware of the threats they could pose on those below.
- By Sydny Shepard
- May 01, 2017

The proliferation of networked devices has increasingly brought IT to the table when discussing physical security.
- By Don Campbell
- May 01, 2017

Bel-Air Bay Club staff gives the system rave reviews and its ability to improve their relationships with club members.
- By Arie Melamed
- May 01, 2017

While the technology can add an effective, additional layer of cybersecurity, it’s not a catch-all. In fact, the very nature of biometric technology can introduce additional security gaps.
- By Alisdair Faulkner
- May 01, 2017

In the world of law enforcement, the subject of body-worn cameras has arguably become the biggest talking point.
- By Greg Buckner
- May 01, 2017
One of the biggest verticals in the security industry is government. Naturally, the federal government comes to mind when this topic is mentioned; however, the government encompasses far more than the feds.
- By Ralph C. Jensen
- May 01, 2017

If you know GardaWorld, it’s likely because you’ve been behind one of their ubiquitous and hard to miss red and white armored trucks as they go about the business of being North America’s largest cash-handling service provider.
- By Daniel Bachmann
- May 01, 2017
Thirty-seven percent of people in the United States bought one or more smart devices in 2015, and many of the people in this large consumer market are tech savvy – so how do you tap into them? Having a broad online presence with positive messaging can help take your business to the next level. But, you may ask, “How do I get started?”
- By Lindsay Lougée
- May 01, 2017
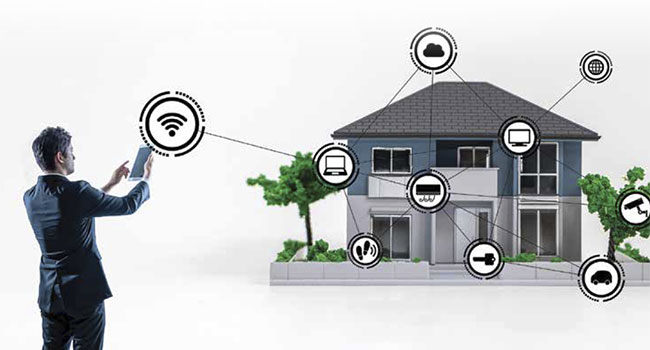
The IT approach to layered security for systems, infrastructure and data is increasingly impacting the security department, and with good reason.
- By Jeff Whitney
- May 01, 2017
I admit there is not a lot in common between ballet and a security installation.
- By Ralph C. Jensen
- May 01, 2017

Police believe the incidents are unrelated.

Philadelphia law enforcement creates plan to secure the NFL Draft.

Chipotle customers may have more to complain about than just an extra cost for guacamole.

Campus carry laws in Kansas have university’s searching for the funds to protect their no-gun zones.
Open Options, the leader in open platform access control solutions, is excited to announce Chris Gouge as the company’s new Southwest US sales manager.
Uber knows where to find you even if you do delete the app.
Cash Deposit Solutions Help C-Stores and Gas Stations of all Sizes Reduce Loss, Increase Efficiencies and Manage Cash Flow

Senator Charles Schumer raised concern about the threat of terrorism at Penn Station.
$100 Million Investment Dedicated to Develop Future Security Innovations

Police in Paris say officers were intentionally gunned down on the popular Parisian avenue.

The Secret Service will enlarge the security perimeter around the White House.
New CNAccess Line Provides up to 32 Door Solution
Mission500, a charitable organization that works closely with the security industry to serve children in need in the U.S., raised more than $125,000 at its eighth annual Security 5K/2K Run/Walk and related sponsorships at this year’s ISC West.

The primary function of a commercial security system is to provide a safe and secure business environment, so everyone can sleep a little easier knowing the business is protected.
- By Jeff Wyatt
- Apr 20, 2017

Police have arrested the suspect who shot and killed three people in downtown Fresno, Calif.

Security will be tight as the people of France elect their next president.
Vanderbilt has announced a new partnership with Citel Spa, a supplier of physical security information management (PSIM) software to Italy’s financial and industrial sector.
Dell EMC OEM Video and Surveillance Products Now Available in
Seneca-bundled Solutions